Is Cloudflare Too Perfectly Priced? Strategic Analysis and Investment Deep Dive ($NET)
In-depth equity research on Cloudflare’s strategic platform ambitions, competitive threats, and long-term investment case
Welcome to Pumice Capital — your free source for in-depth fundamental research on some of the world’s highest-quality companies.
We’re building a concentrated portfolio of resilient, growth-oriented businesses with a 10+ year investment horizon. Our mission: to maximise long-term value through deep, differentiated analysis.
We publish one comprehensive research deep dive each month.
Previous reports: Confluent (CFLT) | Snowflake (SNOW)
If you're passionate about exploring the world’s most transformative companies and want early access to our latest deep-dive reports, subscribe for free below:
In an era where milliseconds define user experience and cyber threats pose constant risks, Cloudflare has evolved from a niche performance project into a critical internet infrastructure provider. Founded in 2009 with a mission to “help build a better Internet,” Cloudflare today operates a global network spanning 335+ cities in 125+ countries, offering enterprise-grade speed, security, and programmability without relying on traditional hardware.
What sets Cloudflare apart isn’t a single dominant moat, but a system of reinforcing advantages: global cost leverage, a tightly integrated product suite that accelerates adoption, and a high-velocity execution culture that enables rapid innovation and deployment. These dynamics combine to create a flywheel effect that strengthens with scale.
However, Cloudflare’s position is not unassailable. Hyperscalers like AWS could commoditize key offerings through aggressive bundling and pricing, while entrenched security incumbents such as Zscaler and Palo Alto Networks maintain deep enterprise relationships and robust product ecosystems that are hard to displace.
In this report, we trace Cloudflare’s journey from a point solution to a full-stack infrastructure platform—unpacking the strategic architecture behind its growth, assessing competitive threats, and exploring how its expanding role at the edge could reshape internet infrastructure.
Table of contents
1 - Why Cloudflare exists: The company’s evolution, strategy, and current role within internet infrastructure
2 - Market growth drivers: An overview of TAM and key factors supporting the market’s long-term growth outlook
3 - Competitive landscape: Who Cloudflare competes with and strengths / weaknesses vs each category
4 - Power analysis: Analysing Cloudflare through the lens of Hamilton Helmer’s 7 powers framework
5 - Strategic risks: Evaluating Cloudflare’s competitive advantages against key existential business risks
Conclusion: Key takeaways and implications for Cloudflare as an investment opportunity
1 - Why Cloudflare exists
Cloudflare began with a simple but unconventional belief: security should not slow the internet down - it should make it faster.
That idea took shape in 2004, when Matthew Prince and Lee Holloway launched Project Honey Pot, an open-source initiative for tracking email spammers. By 2008, it was protecting tens of thousands of websites and logging billions of malicious activities. But there was a clear limitation: they could see threats, but not stop them. That insight opened the door to a bigger ambition - could security be embedded directly into the internet’s infrastructure?
Prince partnered with Michelle Zatlyn, a Harvard Business School classmate, and Holloway to launch Cloudflare in 2009. Their shared goal: build infrastructure that made the internet safer, faster, and more reliable.
“We didn’t set out to build a CDN or a security tool. We set out to build a better internet.” – Matthew Prince, co-founder & CEO
Harder, better, faster, stronger
Early sceptics argued that adding a security layer would slow down websites and create unacceptable latency. This critique fuelled an obsession with speed and performance within Cloudflare’s founding team, and when the beta version launched in June 2010, critics fell silent. Websites didn't just become safer, they loaded 30% faster.
Over the subsequent years, Cloudflare expanded rapidly. Between 2010 and 2016, it launched numerous features and built out a global network, with a core focus on both performance and simplicity.
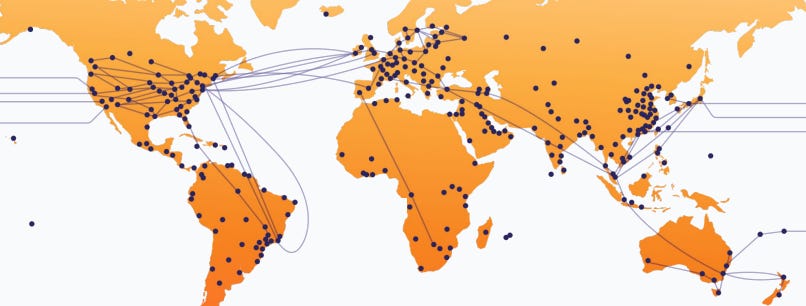
Cloudflare’s network includes datacenters (the blue dots below) and its backbone (lines below, which are fiber optic cables connecting these).
Cloudflare leases space in available datacenters install its servers and networking equipment.
Cloudflare’s network
Two key decisions were pivotal during this early growth phase, setting the foundations for the company today:
Cloudflare's freemium model allowed it to serve millions of small websites at minimal marginal cost by using idle network capacity. These users not only enhanced Cloudflare’s visibility into threats but also provided valuable feedback, enabling rapid product iterations.
Cloudflare's unified architecture - managing DNS, WAF, CDN, and DDoS protection through a single control plane - enabled the instant, global deployment of new features without the overhead of hardware upgrades or fragmented codebases.
Together, these strategic choices propelled viral adoption and provided Cloudflare with structural advantages relative to its competitors.
The connectivity cloud
Initially, Cloudflare’s job was straightforward: protect and accelerate public websites. But as internet infrastructure grew more complex, the company’s ambitions expanded. Rather than just defending websites, Cloudflare set out to secure and optimise all traffic flowing across the internet - covering APIs, internal apps, employee devices, and edge computing environments.
That vision evolved into the Connectivity Cloud: a unified global platform that seamlessly integrates security, networking, and compute. Its core elements include:
Cloudflare One – A Zero Trust suite replacing VPNs and firewalls with identity-aware controls.
1.1.1.1 – A privacy-first DNS resolver prioritising speed and confidentiality.
Workers, R2, KV, D1 – A developer platform enabling global, serverless applications.
Unlike disjointed point solutions, Cloudflare delivers a cohesive architecture where every component is designed to work together by default. Services are delivered through a shared infrastructure, configured via a unified interface, and governed under consistent policy frameworks.
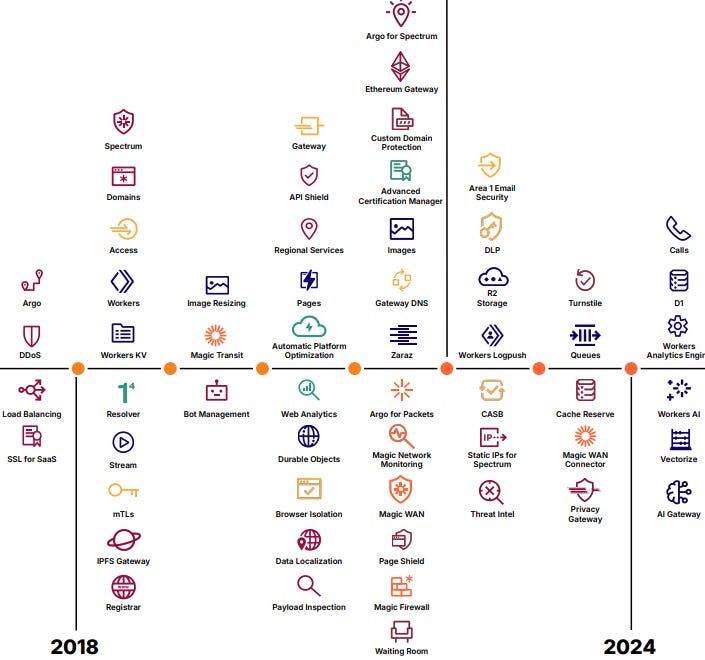
Cloudflare’s product suite over time
The practical benefits are illustrated by customers like Shopify, which relies on Cloudflare to support traffic during Black Friday sales - when transaction volumes reach nearly $4m per minute. Cloudflare helps ensure low latency, operational resilience, and effective DDoS mitigation, all without requiring custom tuning or specialised engineering effort.
This gets to the core of Cloudflare’s value proposition: eliminating complexity. Developers can build without worrying about orchestration. Enterprises can scale globally while enforcing security policies natively in the network. And as adoption deepens, Cloudflare becomes more than infrastructure - it becomes the connective layer underpinning the modern internet.
Becoming the internet’s connective layer requires not just architectural elegance, but alignment with where enterprise infrastructure is heading. We now turn to the structural forces shaping that terrain.
2 - Market growth drivers
Cloudflare operates at the intersection of several structurally expanding markets: Zero Trust security, edge compute, cloud networking, and serverless platforms. Each of these categories alone represents a large opportunity. Together, they signal a broader architectural shift in enterprise IT from perimeter-centric, hardware-defined models to globally distributed, software-defined networks.
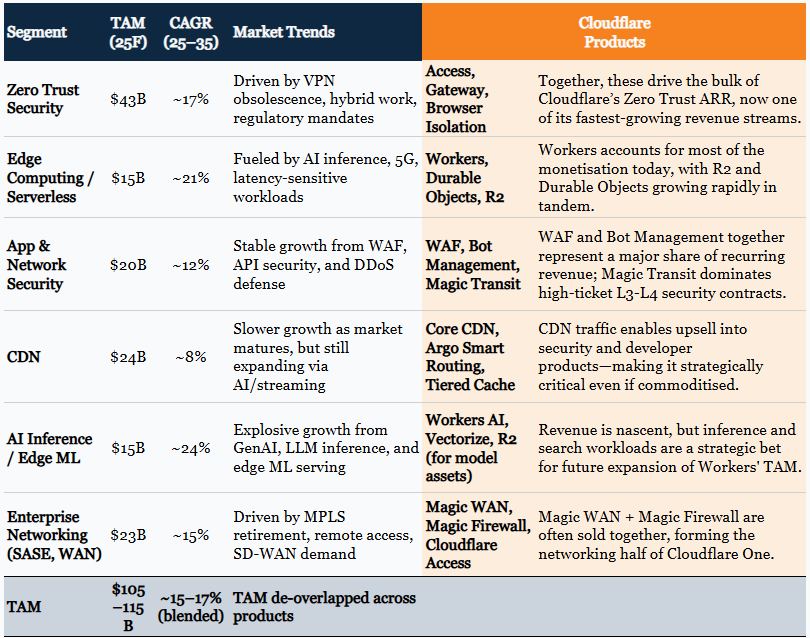
Cloudflare estimates its adressable market at $181b for 2025, we use a more conservative bottom up estimate of $105–115b. This is forecast at >15% p.a. over the next decade. This reflects bottom-up sizing across Zero Trust, edge compute, serverless platforms, and cloud networking, driven by foundational changes in how digital systems are secured, scaled, and operated.
Four key structural drivers underpin this growth trajectory
A) Rapid growth in global internet traffic
Global internet traffic continues to rise sharply, driven by data-heavy applications like video conferencing, high-definition streaming, and generative AI. This growth is both absolute and structural – not just more users, but new types of workloads with more demanding latency and bandwidth requirements.
In 2024, global internet exchanges handled over 68 exabytes of data, up 15% YoY, more than doubling since 2020.
Average monthly smartphone data usage reached 20.3 GB per user in 2024, projected to exceed 23.8 GB in 2025.
AI and LLM-driven services are beginning to account for a meaningful share of global traffic.
This surge places increasing pressure on traditional backbone infrastructure. Enterprises are responding by investing in distributed network architectures, edge compute, and latency-optimised delivery platforms.
Cloudflare product relevance:
CDN, Argo Smart Routing, and Network Interconnect reduce latency and packet loss, optimising performance at the edge.
Workers allows for compute workloads to be executed closer to the user, improving responsiveness for AI inference and real-time applications.
While traffic growth is undeniable, it does not necessarily translate into higher revenue per bit. Much of this traffic (AI training, streaming) risks becoming commoditised unless paired with differentiated value capture. Cloudflare’s edge-native architecture enables value-added services (e.g. programmable routing and security) that preserve margin.
B) The cybersecurity imperative
Cybersecurity threats are growing in frequency, scale, and complexity. Attacks are no longer occasional disruptions – they are persistent, increasingly automated, and often nation-state backed. For enterprises, this has shifted security from a risk management concern to an operational priority.
Cybercrime costs are projected to exceed $13.8t in 2025, growing c.13% YoY.
Automated scan and attack traffic averaged 36,000 requests per second in 2024, up c.17% YoY.
Latin America and Europe saw 53% and 35% YoY increases in attack volumes, respectively.
These dynamics are pushing enterprises to re-architect security from a defensive layer to an embedded system design – where Zero Trust is not just a framework, but a default assumption.
Cloudflare product relevance:
Cloudflare One (Zero Trust platform) integrates access control (Access), browsing security (Browser Isolation), and traffic filtering (Gateway).
Magic Firewall and Bot Management help neutralise volumetric and automated threats.
Security is embedded directly in the edge network, not bolted on—minimising latency and attack surface.
Platforms that embed security into the fabric of network delivery, not just as a patchwork of tools, are becoming the foundation of modern IT environments.
C) Shift toward cloud-native and edge-first environments
Enterprises are migrating from hardware-defined perimeter firewalls and VPNs to identity-based, policy-driven access models delivered as-a-service.
The Zero Trust security market is valued at c.$43b (2025F), with a forecast CAGR of c.17% through 2035.
Cloud-native security and network frameworks accelerated post-2023, driven by remote work, multi-cloud complexity, and compliance mandates.
Latency-sensitive applications—from real-time collaboration to LLM-based interfaces—are demanding edge-first compute models.
Cloudflare product relevance:
Cloudflare Workers and Durable Objects support serverless, edge-native application architectures.
Magic WAN and Magic Transit enable network modernisation without MPLS dependence.
Developer Platform tools allow seamless integration with CI/CD pipelines, crucial for agile teams operating across multi-cloud environments.
Hyperscalers retrofit edge performance into architectures optimised for datacentre gravity - Cloudflare, by contrast, was born at the edge.
D) Regulatory pressure and data localisation
Over 150 countries have implemented or proposed data sovereignty requirements. These rules – often industry-specific and jurisdiction-dependent – place new burdens on infrastructure teams to manage where and how data is stored, processed, and routed.
Jurisdictions like the EU and China impose stringent restrictions on data transfer and cross-border flows.
Enterprises in regulated sectors increasingly seek platforms that can dynamically route and localise traffic by geography.
Cloudflare product relevance:
Regional Services and Geo Key Manager allow data and encryption key localisation to meet jurisdictional constraints.
Data Localisation Suite and policy-based routing provide granular control over how traffic and metadata traverse global infrastructure.
These compliance-oriented features are now gating factors in major RFPs, transforming Cloudflare’s global network from a performance differentiator into a regulatory moat.
A new infrastructure baseline
The enterprise stack is undergoing a fundamental reset. Low latency, embedded security, programmability, and localisation have ceased to be differentiators - they are now table stakes. For vendors, this changes the game: meeting the new baseline is necessary, but insufficient.
Cloudflare is architecturally aligned with this shift. Its Zero Trust platform, developer-native edge tooling, and programmable infrastructure position it as a natural choice for enterprises re-architecting around compliance, performance, and global scale. But technical strength alone won’t decide the outcome.
Winning this layer is about controlling defaults. Distribution, integration, and orchestration, rather than raw capability, will determine who sets the rules.
As the edge becomes the new control plane, platforms are in direct conflict. The battlefield has shifted from packet delivery speed, to policy enforcement, trust mediation, and control over enterprise routing logic. Hyperscalers, incumbent security vendors, and cloud-native challengers are converging on the same chokepoints. The key question is no longer market size, it’s who commands it.
In the next section, we examine where Cloudflare stands in this reconfigured competitive terrain and what it must defend to preserve strategic leverage.
3 - Competitive landscape
Every millisecond shaved from a DNS lookup, every blocked exploit, and every edge function execution brings Cloudflare into collision with hyperscalers, security incumbents and edge-native specialists. With real-time routing, embedded security, and programmable delivery now baseline, the competitive advantage shifts to who governs traffic flows, enforces policy, and anchors developer workflows.
Cloudflare faces a multi-sided attack, with competitors at one end trying to commoditise its products (hyperscalers) and those trying to fragment the stack (cloud-native specialists).
Section summary
Incumbents and legacy rivals
Cloudflare’s early wins came from unseating legacy vendors: CDNs, hardware firewalls, and telecom stacks.
Akamai remains entrenched in high-throughput video and media use cases, where Cloudflare's architecture underperforms.
F5 and Cisco retain hold in regulated sectors and operationally conservative environments through compliance, training lock-in, and contract inertia.
Telcos control last-mile infrastructure and often retain bundled WAN, MPLS, and DNS relationships that shield them from disruption.
Takeaway: The low-hanging fruit is gone, though Cloudflare can still make gains as technology and industry requirements evolve.
Cloud-native specialists
Cloud-native peers exploit specific seams in Cloudflare’s architecture and aim to fragment rather than replace the stack, offering best-in-class point solutions.
Zscaler dominates Zero Trust at scale, with strong SIEM integration, MSSP alignment, and deep enterprise credibility. Cloudflare wins on performance and integration simplicity, but trails on operational depth.
Fastly leads in programmability, offering WASM-native compute and elite developer mindshare. It attracts performance-sensitive users frustrated by Cloudflare’s V8 constraints.
Startups like Temporal and Redpanda pick off edge compute, eventing, or mesh networking use cases where Cloudflare’s primitives feel insufficient or opaque.
Takeaway: These players don’t need to displace Cloudflare, just carve off the most valuable parts. Cloudflare’s unified product suite—its greatest strength—could also be its most exposed flank if customers can get comfortable with the added complexity of stacking competitor products.
Platform competition
While Cloudflare is being squeezed from above by cloud natives, Hyperscalers provide pressure from below. Providing less functional, but essentially free, products, AWS, Microsoft, and GCP don’t need to out-innovate; they win by owning the procurement interface.
Microsoft distorts pricing through aggressive bundling. Security tools within E5 render Cloudflare’s Zero Trust stack functionally “already paid for” in many enterprises.
AWS undermines retention by embedding primitives like CloudFront, WAF, and S3 into the developer workflow, making Cloudflare redundant in many all-in-AWS environments.
GCP subtly shifts standards via control of DNS, Chrome, and Android—shaping what performance and routing “should” look like.
Takeaway: This is a slow burn erosion, not a feature war. Cloudflare’s defence is neutrality and ease of use, but unless it delivers a meaningfully better experience the platform gravity poses a significant threat.
DIY and open-source challengers
Open-source stacks don’t threaten Cloudflare at enterprise scale, but they remain influential in high-performance and engineering-led teams.
NGINX, HAProxy, and mesh VPNs offer fine-grained control and transparency where SaaS feels opaque or inflexible.
Perception gaps around pricing clarity and debugging push some developers toward open alternatives even if the total cost is higher.
Takeaway: Cloudflare wins on reliability, security, and scale, but must maintain developer trust through radical clarity. When control, not convenience, drives decisions, DIY wins.
Incumbents and legacy rivals
Cloudflare faces entrenched competition across multiple fronts: legacy CDNs, on-prem hardware vendors, enterprise security giants, and telcos. Each group commands deep customer relationships and historical mindshare but most struggle to match Cloudflare’s unified, software-native architecture.
To gain ground, Cloudflare pairs bottom-up developer adoption with a growing enterprise sales push. This dual approach has delivered traction, but the harder task now is displacing incumbents in high-assurance, compliance-heavy environments.
Traditional CDN and internet infrastructure
Akamai, the legacy CDN leader, remains entrenched in high-throughput video and OTT workloads due to longstanding contracts, optimised media pipelines, and deep integration with legacy broadcasters.
Where Cloudflare is winning:
Modern web and SaaS workloads: Cloudflare dominates in performance-driven companies like Discord and Notion, with real-time propagation and developer-first ergonomics.
Developer-led adoption: Its freemium model, flat-rate pricing, and frictionless onboarding outmatch Akamai’s heavyweight sales cycle.
Integrated cross-sell: Many customers adopt Cloudflare’s CDN incidentally (through security or compute use) making it the connective layer by default.
Where it is losing:
Media-heavy use cases: Akamai retains dominance in long-form video and live broadcasts, where adaptive streaming, regional peering, and throughput tuning are essential.
Live event infrastructure: Cloudflare’s web-optimised architecture underperforms for high-bandwidth, persistent streams in media-centric geographies.
Strategic focus: Cloudflare should avoid legacy throughput battles and double down on programmable delivery - where value is shifting toward computation at the edge. Enhancing Workers, R2, and AI integration positions it to own the next phase of CDN evolution. Akamai’s edge is baked into legacy contracts; Cloudflare’s is built for modern traffic.
On-premise hardware vendors
Cloudflare directly challenges legacy appliance vendors whose firewalls, VPNs, and ADCs powered pre-cloud enterprise networking. These incumbents retain footholds in regulated sectors via compliance, procurement inertia, and entrenched operational workflows.
Where Cloudflare is winning:
Cloud-native displacement: Zero Trust and Magic Transit are dismantling legacy hardware stacks in favour of programmable, API-first infrastructure.
Cost-led disruption: Flat-rate pricing undercuts vendors like F5, particularly in multi-region deployments.
Developer-centric environments: CLI-heavy appliances struggle in environments optimising for automation and self-service.
Where it is losing:
Regulated industries: Finance, defence, and telecom often require appliance-based control, segmentation, and validated routing - areas where legacy vendors still outperform.
Procurement and training lock-in: Many IT teams are trained on legacy systems, and procurement cycles favour known vendors.
Strategic focus: Cloudflare must evolve from a software-defined alternative into a policy-defined upgrade. Success depends on easing transitions - not just through product, but co-managed onboarding and performance guarantees. Framing itself as an architectural leap, not just a cheaper option, will drive deeper enterprise wins.
Enterprise security software giants
Cloudflare competes with security incumbents who offer broad portfolios across XDR, firewalls, and orchestration. These vendors dominate SOC workflows, procurement cycles, and MSSP ecosystems.
Where Cloudflare is winning:
Integrated simplicity: Mid-market buyers prefer Cloudflare’s unified deployment - DNS, access control, and WAF all governed through one control plane.
Edge-native enforcement: Low-latency policy enforcement at PoPs outperforms regional datacentres for performance-sensitive environments.
Consolidation-led modernisation: Organisations seeking vendor rationalisation gravitate to Cloudflare’s single-platform model.
Where it is losing:
Threat intelligence and response depth: Legacy vendors offer richer telemetry, XDR tooling, and SOC integrations - key for regulated environments.
Support ecosystem depth: MSSP-aligned security stacks remain difficult to displace, especially in Fortune 500 deployments.
Strategic focus: Cloudflare should invest in detection surfaces, SIEM compatibility, and export tooling - not to replicate XDR, but to enhance observability and trust. It wins not through feature parity, but by reducing security’s operational surface area.
Telecom and network service providers
Cloudflare competes with telecom carriers offering MPLS, DNS, WAN routing, and managed security services. These providers retain structural advantages through control of last-mile infrastructure and embedded contracts, particularly in markets with limited ISP competition.
Where Cloudflare is winning:
Displacing MPLS and rigid WANs: Magic Transit enables flexible routing and DDoS protection at lower cost, especially attractive for multinational, cloud-native firms.
Edge performance in underserved geographies: Cloudflare’s Anycast model consistently delivers lower latency than telcos with centralised architectures.
Programmability and control: Telco-managed networks remain opaque and inflexible. Cloudflare offers policy-driven routing and visibility, appealing to DevOps-led environments.
Where it is losing:
Legacy contracts and inertia: Many global enterprises are locked into multi-year WAN deals bundled with voice/data services.
Bandwidth gatekeeping: In weak net neutrality markets, telcos can prioritise traffic from favoured CDNs, subtly disadvantaging Cloudflare.
Lack of physical infrastructure: Cloudflare leases rather than owns fibre, limiting leverage in certain edge cases.
Strategic focus: Cloudflare must continue turning telcos from competitors into distribution partners - offering peering incentives and shared caching infrastructure to reduce last-mile costs. Where telcos sell rigidity, Cloudflare must sell optionality. It doesn’t need to own the pipes, just redefine how they’re used.
Cloud-native specialists
While Cloudflare has spent the past decade chipping away at legacy incumbents, its most formidable strategic threats now come from peers not predecessors. These challengers are cloud-native, product-led, and often more focused in scope, enabling them to move faster in specific categories.
Some, like Zscaler, are already entrenched in enterprise security. Others, like Fastly, bet on differentiated edge compute models. A new generation of startups are probing around the edges competing on technical nuance, developer affinity, or regulatory positioning.
These players don’t need to displace Cloudflare entirely to hurt it. They only need to fragment the stack - slowing convergence, siphoning high-margin verticals, or raising switching costs. In this environment, Cloudflare’s greatest strength (its unified platform) also becomes its most exposed flank which incentivises rivals to specialise and siphon discrete high-margin functions without replicating the whole.
The following subsections examine each class of disruptor, and where the structural risk lies.
Zscaler and zero trust competitors
Zscaler is Cloudflare’s most direct peer in the Zero Trust category. Unlike legacy security vendors, Zscaler was cloud-native from inception, positioning itself as a secure internet access and private application gateway platform. Its multi-tenant, proxy-based architecture closely mirrors Cloudflare One’s ambition but with greater maturity in large enterprise deployments.
Where Cloudflare is winning:
Performance and global edge reach: Cloudflare enforces policy at every PoP, outperforming Zscaler’s region-based nodes for distributed teams.
Unified platform value: Cloudflare bundles security, routing, and observability in a single interface - appealing to mid-market buyers seeking simplicity.
Developer affinity: Zscaler lacks programmability. Cloudflare’s edge-native developer tools unlock new security-plus-app workflows.
Where it is losing:
Enterprise security depth: Zscaler dominates six-figure Zero Trust deals via deep compliance, SIEM integrations, and security operations credibility.
Sales execution at scale: Zscaler’s high-touch GTM outpaces Cloudflare in Fortune 500 security-led accounts.
Strategic focus: Cloudflare must resist mimicking Zscaler’s complexity. Its advantage lies in convergence - offering security not as a silo but as part of a programmable network fabric. Enhancing SIEM compatibility and threat visibility will improve fit without compromising simplicity.
Fastly and edge computing specialists
If Zscaler challenges Cloudflare on the security front, Fastly poses the sharpest threat on the programmable edge compute frontier. Unlike traditional CDNs, Fastly built its platform with developers in mind, emphasising custom logic, real-time control, and low-level performance. Its Compute@Edge platform uses WebAssembly for ultra-fast, sandboxed execution, contrasting with Cloudflare Workers’ JavaScript-first, V8-based model. This technical divergence represents a core battleground for developer mindshare.
Beyond Fastly, a wave of smaller challengers (Section.io, Edgio, and Netlify’s Edge Functions) are carving out positions at the intersection of CDN, CI/CD, and edge execution. Though smaller in scale, these players exploit points of friction in Cloudflare’s architecture to attract early adopters and niche communities.
Where Cloudflare is winning:
Distribution and scale: Cloudflare’s 335+ PoPs deliver superior consistency outside core metros.
Platform breadth: Workers, R2, KV, and D1 form a comprehensive edge stack rarely matched by Fastly’s narrower focus.
Security leverage: Fastly lacks Cloudflare’s security layer, making it harder to compete on end-to-end infrastructure convergence.
Where it is losing:
Programmability depth: Fastly supports more languages and low-level logic, giving it the edge in performance-sensitive edge applications. If WebAssembly becomes the standard for secure, high-performance edge workloads, Cloudflare’s V8 runtime may face obsolescence risk. Fastly’s WASM-native architecture is better aligned with that future and could pull ahead if developer expectations shift.
Developer credibility: Among elite engineers, Fastly is viewed as the more open, performant option - especially where Cloudflare’s runtime feels limiting.
Strategic focus: Cloudflare must close the programmability gap without compromising ease of use. Continued investment in runtime flexibility, debugging, and developer transparency will be critical to hold the high end.
Niche startups and emerging challengers
Beneath the surface of high-profile competitors lies a more fragmented but potentially destabilising tier: startups and point-solution specialists. These firms are not attempting to replicate Cloudflare’s platform wholesale but are targeting specific areas where speed, transparency, or depth is lacking. Whether in observability, edge AI, or data privacy, they create risk not through scale, but through disruption of architectural cohesion.
Examples include:
Bunny.net – targeting developer-led CDNs with transparent pricing and better user experience.
Netbird, Tailscale – peer-to-peer Zero Trust networks exploiting simplicity and mesh-based architecture.
Redpanda, Upstash, Temporal – edge-native data and state management tools designed to outperform Cloudflare’s current storage and event frameworks.
Where Cloudflare is winning:
Unified surface area: Few rivals offer storage, compute, and security as a coherent whole. Cloudflare remains the go-to for teams seeking integration over piecemeal tools.
Global reliability: Startups rarely match Cloudflare’s SLA guarantees, PoP scale, or DDoS protection.
Where it is losing:
Developer trust at the margin: Perceptions of opacity (around pricing, throttling, or debugging) drive some users to leaner, more transparent alternatives.
Ecosystem gaps: For AI inference, durable jobs, or stateful coordination, startups like Temporal or Redpanda offer stronger primitives.
Strategic focus: Cloudflare must foster trust through clarity on pricing and runtime behaviour. Supporting external integrations and open patterns will mitigate churn to niche stacks.
Platform competition
Hyperscalers control the ecosystems in which Cloudflare operates. They don’t need to win on product, they win on defaults, bundling, and procurement gravity. The risk is not sudden churn, but strategic erosion: Cloudflare becoming unnecessary before it is unseated.
Microsoft
Microsoft’s $20b+ security business thrives on bundling. E5 licensees inherit Entra ID, Defender, and Purview - tools few actively choose, but many use by default.
Where Cloudflare is winning:
Multicloud and neutrality: Teams avoiding Azure lock-in prefer Cloudflare’s vendor-agnostic model with consistent performance across clouds.
Performance-sensitive apps: Azure’s network prioritises intra-cloud latency; Cloudflare outperforms for public-facing, latency-critical traffic.
Where it is losing:
Cost-conscious enterprises: Microsoft wins by pricing to zero - Cloudflare can’t compete with “already paid for.”
Identity stack integration: Entra ID is deeply embedded in enterprise auth flows; Cloudflare layers on top, not underneath.
Strategic focus: Cloudflare must anchor on neutrality and transparency. For regulated, multicloud customers wary of platform lock-in, it offers clarity where Microsoft offers opacity.
AWS
AWS competes directly on primitives (CDN, WAF, DNS, DDoS, object storage) making Cloudflare’s value harder to isolate in all-AWS stacks.
Where Cloudflare is winning:
Global edge performance: Cloudflare’s PoP footprint is broader and more granular than CloudFront’s regional model.
Ease of use: AWS interfaces are powerful but siloed; Cloudflare offers unified policy management and faster time to value.
Data economics: R2’s zero-egress pricing contrasts sharply with S3’s punitive exit fees - especially for bandwidth-heavy apps.
Where it is losing:
Operational inertia: Many teams simply build everything inside AWS. Native integration trumps marginal performance in low-stakes workloads.
Marketplace friction: Cloudflare often requires separate procurement cycles; AWS Marketplace streamlines onboarding and billing.
Strategic focus: Cloudflare must position itself as the connective layer across clouds. Winning isn’t about outperforming AWS inside its castle - it’s about being indispensable outside of it.
Google Cloud Platform (GCP)
GCP’s threat is more systemic than commercial. It shapes internet architecture through Chrome, Android, and DNS infrastructure - setting defaults more than it sells.
Where Cloudflare is winning:
CDN and edge execution: GCP’s edge stack remains limited. Cloudflare leads in performance, particularly for API-driven and global applications.
Developer visibility: Workers enjoys greater traction in JAMstack and edge-first communities.
Where it is losing:
AI and data gravity: As inference moves to the edge, GCP’s model-serving and data tooling will attract builders seeking integrated pipelines.
Protocol influence: Google’s role in DNS resolution and browser behaviour gives it outsized influence over routing and performance expectations.
Strategic focus: Cloudflare must differentiate on openness. It cannot out-standard Google, but it can become the neutral alternative for teams that fear platform overreach.
DIY and open-source
DIY and open-source solutions rarely threaten Cloudflare at scale but appeal to engineering-led teams seeking fine-grained control or vendor independence. These stacks (typically built on NGINX, HAProxy, or mesh VPNs) win not through features but by offering perceived transparency, flexibility, or cost savings.
Where Cloudflare is winning:
Operational simplicity: Most companies lack the appetite to manage TLS, DDoS mitigation, and global routing. Cloudflare packages this into a unified, fully managed stack.
Observability and integration: Open-source setups often require stitching together disparate tools. Cloudflare’s control plane simplifies operations and debugging.
Resilience and coverage: Cloudflare’s ability to absorb large-scale attacks with sub-second mitigation is virtually unmatched in self-hosted environments.
Where it is losing:
Control-focused engineering orgs: High-performance teams may still prefer tuning their own stack, particularly in performance-sensitive or compliance-heavy contexts.
Cultural distrust of SaaS: Some developers remain sceptical of closed, centralised platforms—especially where pricing or policy clarity is lacking.
Strategic focus: Cloudflare must demonstrate that DIY carries higher long-term costs - not just in money, but cognitive and operational overhead. Transparent pricing, API-level interoperability, and reliability metrics will help it win over pragmatic engineers who might otherwise default to OSS.
Cloudflare’s competitive map spans every layer of the modern internet stack. Some threats are immediate and tactical. Others, like platform erosion or developer churn, move slowly but reshape the terrain over time. The company’s ability to withstand this pressure depends less on any single feature, and more on the compound advantage of its integrated platform.
To evaluate the durability of these defences, we must now turn from competitive tactics to strategic foundations. The question is not who Cloudflare outperforms today - but whether its structural advantages can scale, entrench, and resist erosion over the long term. We now assess Cloudflare’s positioning through the lens of strategic power.
4 - Power analysis
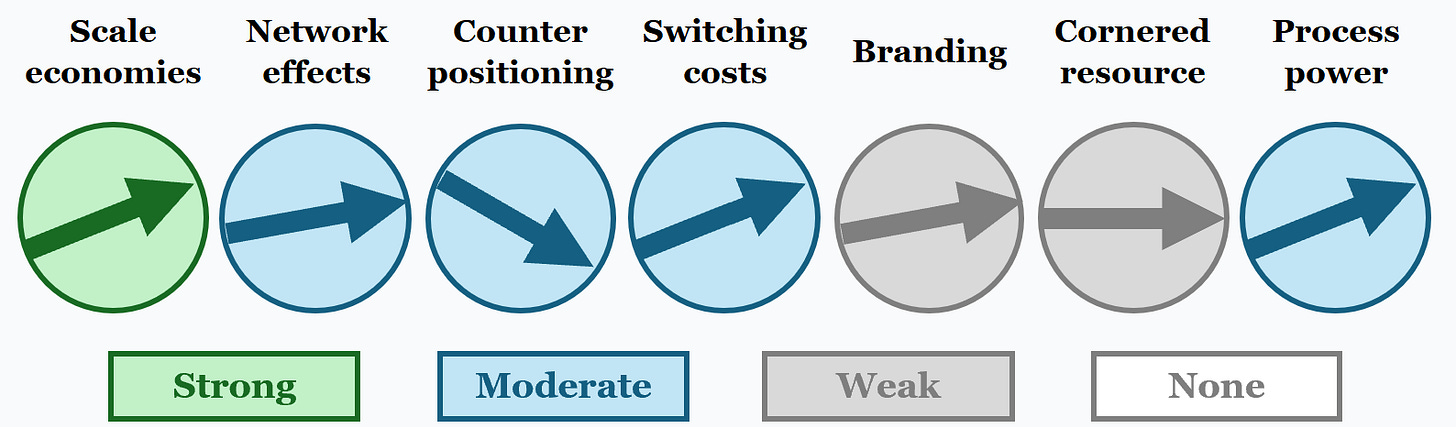
To assess the durability of Cloudflare’s strategic advantage, we apply Hamilton Helmer’s “7 Powers” framework. Cloudflare does not rely on any one of these alone, but instead benefits from multiple overlapping sources of strength, each at different levels of maturity.
Scale economies
Definition
Scale economies emerge when marginal costs decline faster than rivals can match - producing an unreplicable cost structure.
Rating: Strong (Increasing)
Cloudflare clearly exhibits this dynamic across infrastructure, engineering leverage, and go-to-market reach. The critical test is not whether it operates at scale, but whether that scale yields structurally advantaged unit economics. Against this bar, Cloudflare stands apart from smaller peers and even challenges hyperscalers in select domains.
Cloudflare’s global network spans 335+ cities, with close to 400 Tbps capacity. These edge nodes form the economic engine behind flat-rate pricing, free tier offerings, and real-time mitigation at a fraction of competitor cost. Every incremental domain, API, or Worker function improves asset utilisation and amortises core infrastructure.
This structural advantage manifests in three interlocking ways:
Cost per bit and request: Cloudflare absorbs multi-terabit DDoS attacks without surcharge, while most vendors rely on burst pricing or capacity reservations. At $20/month, its Pro plan offers protections that would be financially ruinous for peers like Bunny.net or Fastly to replicate without incurring losses.
Custom hardware and orchestration: Cloudflare avoids proprietary boxes, instead using commodity servers and its own high-efficiency stack. Features like Auto Placement and intelligent load distribution mean each server processes more requests per watt and dollar than rivals. This improves gross margins and enables faster global rollouts.
Peering leverage: Its traffic scale unlocks favourable interconnects and co-location inside ISP facilities. Smaller vendors lack this bargaining power and must route via more expensive paths or suffer higher latency. Even AWS and GCP, while vast, optimise for internal workloads and not low-margin edge services. Cloudflare’s neutrality and focus allow better routing economics at the internet’s edge.
But the scale moat isn’t just physical. Cloudflare has created developer scale - amortising R&D across millions of users and benefiting from vast telemetry to refine security and performance features faster than security peers like Zscaler or edge specialists like Fastly. Each code push impacts trillions of requests, compounding the returns on innovation.
The power is real, but not unassailable. Key risks:
Hyperscaler price aggression: AWS could slash CloudFront and WAF prices to blunt Cloudflare’s cost edge, particularly in bundles. However, Cloudflare’s platform cohesion and neutral positioning make it more accessible for multi-cloud and API-centric workloads.
Diminishing geographic returns: With over 95% of global traffic already served within 50ms, adding new PoPs now delivers only marginal latency improvements. Cloudflare’s strategy is evolving from expanding geographic reach to deepening functional capabilities, like enabling AI inference at the edge. This shift helps preserve scale advantages even as horizontal expansion slows.
Capex burden if traffic flattens: Flat-rate pricing depends on rising traffic and stable capacity utilisation. If traffic plateaus or AI workloads consolidate back into hyperscaler centres, Cloudflare could face underused infrastructure. For now, its pricing discipline and forward provisioning mitigate this.
In practical terms, Cloudflare’s scale advantages force competitors into asymmetric trade-offs:
Fastly’s programmable edge excels technically, but lacks scale to offer comparable pricing or breadth.
Zscaler dominates in deep enterprise Zero Trust, but its infrastructure model doesn’t benefit from the same broad network amortisation.
Microsoft and AWS have superior capital budgets but must optimise across broader priorities, making Cloudflare more agile at the edge.
Put simply, scale isn’t just about being big - it’s about being bigger where it matters. Cloudflare’s architecture, pricing, and market orientation turn that bigness into strategic leverage.
Network effects
Definition
Network effects arise when the value of a product increases with each additional user.
Rating: Moderate (Stable to Slightly Increasing)
Unlike social platforms or marketplaces, Cloudflare’s network effects are indirect, invisible to most users, and often underestimated. Yet they play a growing role in sustaining its platform advantage - particularly in security, performance, and developer experience.
The strongest manifestation lies in threat intelligence. Every new domain, API, or app onboarded contributes telemetry that feeds Cloudflare’s real-time mitigation systems. When an attack hits one target, countermeasures propagate globally within seconds. This immune-system dynamic is only possible with mass-scale diversity - something niche providers cannot replicate. In effect, Cloudflare defends its users with the aggregated experience of trillions of daily requests.
This scale also sharpens its performance optimisation loop. Argo Smart Routing dynamically selects optimal paths based on real-time network conditions. More traffic means better models. While routing engines exist elsewhere, few operate with comparable signal density or in as many geographies. The result is consistently low latency and lower volatility, even during global congestion events.
The third, less obvious, vector is developer ecosystem compounding:
There are now more than 3 million developers on the Cloudflare platform - nearly 10x over the last 5 years. As more developers use Workers, KV, and R2, the pool of shared templates, libraries, and patterns deepens.
Ecosystem integrations (e.g., analytics, observability, deployment tooling) increase, improving time to value for new users.
A growing user base attracts education content, community projects, and third-party add-ons that reinforce Cloudflare as the default starting point.
This resembles a platform gravity well. Even if switching is technically easy, Cloudflare becomes the path of least resistance. Workers may not yet rival AWS Lambda in ecosystem breadth, but for edge-native workloads, the network effects are self-reinforcing.
However, these effects are not bulletproof:
Opacity and ecosystem friction: Unlike companies like GitHub or Snowflake, Cloudflare’s network benefits are mostly hidden. Customers benefit passively, but rarely feel the network improving with scale. This weakens user affinity and underplays the value proposition in procurement cycles.
Narrow scope of direct interdependence: Unlike true network businesses, Cloudflare’s value is not contingent on peer density. A CDN user gains from global insights, but not from who else is on the platform. This limits virality and reduces barriers to churn.
Commoditisation pressure: Hyperscalers like AWS wield rich internal telemetry and could replicate global routing or DDoS intelligence over time. If threat intelligence becomes standardised (via shared feeds or open-source proxies) the edge could erode.
Critically, the most investor-relevant question is not whether Cloudflare’s network effects are strong in isolation, but whether they compound with other powers. Here, the answer is clearer: the more domains it secures, the more data it captures, the more it improves routing and mitigation, the more developers trust it, the more integrations accrue, and so on. These loops are slower than consumer networks, but deeply synergistic.
Over time, new products like AI inference, queue-based messaging, and multi-tenant observability could widen the interdependence of workloads and intensify these network effects. But for now, they remain a moderate moat: real, compounding, but not immune to disruption.
Counter-positioning
Definition
Counter-positioning occurs when a challenger adopts a business model that incumbents cannot emulate without damaging their core economics. It is only a lasting source of advantage if the incumbent’s inaction remains structurally rational - driven by cannibalisation risk, internal conflict, or strategic constraint.
Rating: Moderate (Decreasing)
At inception, Cloudflare was classically counter-positioned: a software-first architecture, flat-rate pricing, and self-serve onboarding that made it economically irrational for incumbents to respond. Akamai couldn’t offer $20/month unmetered DDoS without imploding its enterprise margins. Cisco couldn’t launch a programmable Zero Trust suite without cannibalising hardware sales and partner channels.
But counter-positioning is a transient moat. Its durability hinges on whether incumbents remain structurally paralysed, and that window is narrowing fast.
In security, legacy vendors have embraced cloud delivery. Palo Alto’s Prisma, Fortinet’s SASE suite, and Zscaler’s Zero Trust platform have all evolved beyond boxes.
In CDN, Akamai has adopted programmable edge and now markets AI-powered acceleration and security integrations. Even hardware stalwarts like F5 are offering cloud-native, subscription-based services.
As such, counter-positioning is no longer a primary moat for Cloudflare. It was essential to its early disruption and still opens doors in margin-heavy markets, but its durability is fading.
Continued advantage depends less on incumbent paralysis and more on Cloudflare’s ability to out-execute across scale, process, and ecosystem lock-in.
Switching Costs
Definition
Switching costs refer to the financial, technical, or psychological friction a customer faces when changing providers. High switching costs discourage churn by embedding the service deeply into customer operations - either through complex integration, sunk time, or risk of disruption.
Rating: Moderate (Increasing)
As customers expand their use of Cloudflare’s platform, its services become integrated into production infrastructure and compound over time. A firm using Cloudflare for DNS, WAF, API gateway, Workers, and Zero Trust faces a multi-team, multi-month migration to unwind. This burden is rarely justified by price alone, especially given the operational risk of getting it wrong.
Key factors include:
Runtime dependency: Apps built on Workers using KV, Durable Objects, or Queues are non-trivial to port. Rewriting for Lambda@Edge or Fastly Compute@Edge often requires architectural changes, especially for stateful or latency-critical logic. The more edge-native a workload becomes, the harder it is to decouple.
Integrated security stack: For customers using Zero Trust access, Gateway, and WAF together, the policies, logging flows, and enforcement points are tightly embedded into security workflows. Migrating to Zscaler or Palo Alto equivalents means replicating not just configurations, but deeply ingrained operational practices, and risking security drift during transition.
Process inertia: Enterprises invest in tuning, automation scripts, custom integrations, and staff training. Even if a rival offers equivalent features, the hidden costs of retraining and revalidation can outweigh the gains. One mid-sized SaaS firm that attempted to replace Workers and KV with Fastly Compute and self-hosted Redis found the migration took three months and introduced subtle latency bugs that delayed rollout and forced re-architecture - underscoring the real cost of exit.
These frictions are not absolute. Key caveats include:
Portability by design: Cloudflare avoids proprietary formats and supports open standards. It doesn’t trap customers with closed tooling or opaque data models. This keeps switching possible, but not painless.
Commodity-like core: At the CDN layer, switching costs remain low. Customers can and do swap in Fastly, Akamai, or even DIY stacks for basic delivery or caching. Retention here depends more on price/performance than entrenchment.
Segmented usage: Many customers adopt Cloudflare tactically, e.g. using Workers but not security, or CDN but not DNS. The more fragmented the usage, the lower the effective switching burden.
Overall, while no single component is unbeatable, the bundle is deeply entrenched and hard to replicate in full. For now, switching costs remain moderate, but increasingly act as quiet, accumulating cement beneath the platform.
Branding
Definition
Brand power arises when intangible associations (trust, identity, prestige) compel customers to choose a product even when viable alternatives exist. A true brand moat allows companies to win or retain customers despite functional parity, and ideally justifies price premiums based on perception alone.
Rating: Weak (Slightly increasing)
Cloudflare commands respect among developers: its brand signals reliability, transparency, and modernity, but not margin protection. Among engineers, the company often serves as the default for DNS, WAF, and CDN, purely because of familiarity and reliability. Its educational blog posts, public postmortems, and open documentation build trust. For many, choosing Cloudflare signals modernity and sound technical judgment.
This manifests in several subtle ways:
Trial preference: When evaluating new infrastructure, teams often begin with Cloudflare - not because it’s the cheapest or deepest, but because “it just works” and is safe to try.
Cross-product extension: Existing users frequently expand usage into Workers, R2, or Zero Trust - trusting Cloudflare to deliver on simplicity and cost-predictability.
Mid-market comfort: Buyers without deep security or networking teams rely on Cloudflare as a one-stop-shop. Its brand as an “internet utility” de-risks procurement.
However, these dynamics do not rise to the level of durable brand power. The brand opens doors; it doesn’t close them to rivals.
No pricing leverage: Cloudflare competes on value and transparency, not premium pricing. Customers switch for features or economics, not loyalty. Brand affinity does not protect margins.
No identity attachment: Unlike Apple or even Snowflake, Cloudflare lacks aspirational status. Customers do not signal status or ethos by being on Cloudflare. If a faster, cheaper, or better-integrated option emerges, they will consider it.
Not category-defining: In Zero Trust or edge compute, Cloudflare is still building awareness. In many large-enterprise RFPs, Zscaler or AWS are assumed before Cloudflare is even considered.
Brand power may increase over time, especially if Cloudflare maintains engineering excellence and becomes the default edge platform across categories. But the moat remains shallow. The brand supports conversion, but doesn’t prevent churn.
Crucially, Cloudflare’s brand works best when reinforced by product strength. A few high-profile outages, opaque pricing moves, or stagnation in core products could materially damage perception. In this sense, the brand is a force multiplier, not a shield.
In sum: Cloudflare’s brand does not confer pricing power or deep loyalty, but it reliably drives trial, developer trust, and lateral product adoption. It greases adoption, not pricing power: a persuasive brand, but not a protective one. While weak by Helmer’s strict standards, the brand remains a meaningful force multiplier across Cloudflare’s broader platform strategy.
Cornered resource
Definition
A cornered resource is an asset (legal, contractual, or structurally embedded) that confers exclusive control and materially strengthens competitive position. It must be truly irreplicable, such that no competitor can access it, even with sufficient capital or will. Classic examples include proprietary IP, exclusive supply rights, or deeply embedded founder credibility.
Rating: Weak (Stable)
Nothing Cloudflare controls is off-limits to well-funded competitors. ISPs will peer with any provider of sufficient scale. Colocation centres are open to any firm with capital. Its DNS dataset, while immense, is not proprietary in a way that rivals like Google or Akamai couldn’t match. Even threat telemetry, a notional advantage, is rivalled by Zscaler’s enterprise-heavy dataset or AWS’s internal visibility across its cloud stack.
Three candidate resources fall short on scrutiny:
Talent and engineering culture: Cloudflare is known for rapid shipping and technical depth, But the talent it attracts is neither exclusive nor structurally cornered - its engineering depth reflects process and culture more than access to singular minds or protected IP.
Traffic intelligence: Cloudflare handles trillions of requests per day, feeding into its bot detection, DDoS mitigation, and routing models. But this data advantage is horizontal - hyperscalers have similar or better visibility within their own ecosystems. The insight derived from this traffic is valuable, but not uniquely inaccessible.
Founding credibility: CEO Matthew Prince is an effective spokesperson and public advocate. However, founder-driven narrative strength is not the same as a cornered asset. His influence supports brand and agility, but could be replaced or replicated in effect.
Contrast this with companies like ASML (exclusive lithography patents) or TSMC (process IP and geographic scarcity), where access to the resource is contractually or physically locked. Cloudflare operates in open infrastructure territory - its advantage is in how it executes, not what it alone possesses.
Importantly, Cloudflare has avoided resource cornering by design. Its architecture is open, neutral, and standards-driven. This supports interoperability, but at the cost of exclusivity. It cannot force vendor lock-in through format control, proprietary APIs, or licensing regimes, as Oracle or Palantir do.
Could cornered resources emerge over time? Possibly, especially in areas like:
AI inference at the edge, if paired with proprietary model tuning or data localisation IP.
Integrated observability pipelines that capture unique diagnostic data beyond what hyperscalers expose.
Sovereign-compliant network layers, if Cloudflare becomes a regulatory default in data-restricted geographies.
But these remain speculative. For now, the company’s strategic strength lies in operational excellence, integration depth, and developer affinity - not in exclusive control over critical assets.
Process power
Definition
Process Power arises when a company embeds tacit knowledge, unique workflows, and cultural routines into its operations that yield consistently superior outcomes. These processes must be hard to observe and difficult to replicate, even when rivals attempt to mimic inputs. Genuine process power is rare and often invisible - seen only in the outputs.
Rating: Moderate (Increasing)
Cloudflare’s product velocity and operational execution suggest process power is emerging, though it has not yet reached truly unassailable depth.
Few companies of comparable scale ship faster, iterate more frequently, or experiment as broadly. Cloudflare regularly launches multiple features per quarter across disparate domains - security, networking, storage, compute, AI inference. This velocity is not a function of size, but of design.
Key elements underpinning this include:
Unified architecture: A single codebase and control plane allows every product to interoperate by default. Features are instantly deployable across the global edge network without versioning issues, patch windows, or fragmented support teams.
Developer-led workflows: Cloudflare’s internal systems prioritise modularity and testability. Its engineering teams build tooling not just for end-users but for internal deployment - accelerating QA, rollback, and instrumentation. This has allowed the company to scale product lines without bloating coordination costs.
Cultural alignment: The company’s public-facing transparency (technical blogs, detailed incident reports, and roadmap disclosures) is mirrored internally. Engineers have unusually broad context and autonomy. This creates a flywheel where customer feedback, telemetry, and product evolution are tightly looped.
These practices show up in outputs. Consider the rapid expansion of Workers from a niche JS runtime into a full edge development platform, complete with KV, R2, Queues, Durable Objects, D1, and AI inference - all rolled out in under four years. Or the consistent ability to underprice hyperscalers on bandwidth and storage without degrading performance, a feat requiring not just capex discipline but deep operational coordination.
However, this power is still maturing:
Transparency dilutes defensibility: Cloudflare openly documents its architecture. This means best practices are visible and replicable. Fastly, AWS, and others can mimic the design, even if not the rhythm.
Execution is not yet outcome-insulated: Cloudflare’s success is still visible in features and roadmap pace, not in consistent financial outperformance or category leadership across all products. Until process depth consistently translates into market dominance, the power remains emergent.
Key-person reliance risk: Much of Cloudflare’s operational coherence stems from a tightly aligned founding team still in place. If this leadership transitions, it’s unclear whether the culture and systems would persist or fragment.
That said, process is compounding. As Cloudflare expands its edge stack and deepens integrations across services, the internal benefit of its execution model grows. New products are easier to build, test, and deploy because the infrastructure beneath them is coherent and battle-tested. This feedback loop mirrors what Snowflake built in analytics or what Shopify built in commerce - a foundational substrate that accelerates adjacent expansion.
In summary, Cloudflare’s internal machinery enables faster, more cohesive execution than most competitors. It’s not yet an unassailable moat, but it is a real and growing source of strategic leverage, especially as rivals struggle with siloed architectures, fragmented teams, or partner-channel friction. With time, this may become the company’s most defensible power.
Cloudflare’s strategic strengths, particularly its scale efficiencies, growing switching costs, and executional velocity, form a credible platform moat. Yet durable advantage does not imply immunity.
The right question shifts from “What does Cloudflare do well?” to “Where and how might it fail?” In the next section, we critically stress-test the company's strategic defences - challenging each source of advantage against plausible threats, investor scepticism, and asymmetric risk.
5 - Strategic risks
Strategic advantage is only as durable as the pressures it withstands. Cloudflare’s defensibility, while multi-faceted, faces credible risks across platform erosion, economic compression, and strategic misexecution. In this section, we evaluate not only where Cloudflare could falter, but whether its model has built-in resilience or structural brittleness.
A) Platform erosion by hyperscalers
Cloudflare’s biggest existential risk is from AWS, Microsoft, and GCP. These companies don’t need to beat Cloudflare on features, they can win through bundling, procurement integration, and owning the control plane where infrastructure decisions are made.
Bundling economics: Microsoft’s inclusion of security tools in E5 shifts buyer logic from “best-of-breed” to “already paid for.” AWS offers bandwidth discounts and architectural guidance that make CloudFront the default within its ecosystem. Cloudflare can appear costly in comparison.
Procurement defaulting: Teams provisioning infrastructure inside AWS or Azure face friction in introducing third-party services. Marketplace integration, billing consolidation, and support entitlements make hyperscaler-native tools the path of least resistance.
Ecosystem asymmetry: Hyperscalers control developer workflows, observability layers, and increasingly AI/ML pipelines. Cloudflare cannot compete across this breadth. Its strength is neutrality, but that advantage is only noticeable when customers care. In many cases, they don’t.
This risk is structural and slow-burning. It won’t show up as sudden churn, but as reduced expansion, fewer Greenfield wins, and increasing dependency on developer affinity rather than procurement logic.
Cloudflare’s defence, multi-cloud positioning and focus, is rational but insufficient on its own. To resist erosion, it must offer a meaningfully better experience outside the hyperscaler castle. That means faster, cheaper, simpler, and more cohesive.
B) Limited Zero Trust expansion
In Zero Trust, Cloudflare faces a pincer attack: Zscaler from above, Microsoft from below.
Zscaler dominates six-figure enterprise deployments. Its deep compliance, integration with SIEM/SOAR tooling, and high-touch sales execution make it nearly untouchable in regulated, high-assurance accounts. Cloudflare may match on features but lags on credibility and service assurance.
Microsoft bundles Zero Trust tooling into E5 at near-zero marginal cost. For many security leaders, this renders standalone alternatives hard to justify - even if Cloudflare outperforms technically.
Sales execution risk: Cloudflare’s bottom-up traction doesn’t naturally convert into six-figure expansion. Many Zero Trust deployments require security champions, internal change management, and cross-department orchestration. Cloudflare’s ability to scale that playbook remains unproven at the enterprise tier.
Cloudflare is caught between a rock and a hard place: Zscaler defends the high ground with deep enterprise entrenchment, while Microsoft captures the low ground through costless bundling and ecosystem gravity. Both make it difficult for Cloudflare to scale into the enterprise Zero Trust market without a step-change in go-to-market strategy and credibility.
The risk is twofold: growth stalls if Cloudflare can’t win larger accounts, and margins compress if it’s forced to discount heavily or over-serve lower-paying customers. Until it proves it can reliably execute six-figure Zero Trust expansions, Cloudflare’s enterprise ambitions remain more promise than proven.
C) Edge compute and programmability risk
Edge compute is where Cloudflare is most technically exposed. Fastly, AWS, and a constellation of startups all compete for developer mindshare in the emerging programmable edge.
Fastly wins on performance depth, language flexibility (WASM support), and transparency. Elite engineering teams often view it as the technically superior platform, especially for high-throughput, latency-sensitive workloads.
AWS offers broader integration. Developers building in Lambda, Step Functions, or Bedrock often stay inside the walled garden. Cloudflare must provide both technical and workflow advantage to justify a dual-stack.
Developer trust risk: Cloudflare has occasionally been opaque around throttling, debugging support, and runtime behaviour. In edge compute, these concerns are magnified. Developers value control and clarity—traits Fastly and open-source alternatives often deliver better.
Failure here risks not just margin loss but strategic reclassification from edge platform to utility CDN. Without traction in high-value, programmable use cases, Cloudflare’s pricing power and product roadmap will be constrained by its infrastructure roots.
D) Margin compression and commoditisation
Even if Cloudflare retains customers, it may struggle to monetise usage growth profitably, especially in its foundational services.
Flat-rate risk: Many of Cloudflare’s offerings (e.g. CDN, DDoS protection) operate on flat-rate models. While these drive adoption and loyalty, they cap revenue upside from bandwidth-heavy workloads like AI inference or streaming.
Traffic mix shift: As traffic skews toward heavier, less value-dense content (e.g. model queries, video), cost-to-serve may rise faster than pricing flexibility - especially if customers remain price sensitive.
Benchmarking pressure: Infrastructure buyers increasingly compare on price-per-bit and cost-per-request. Hyperscalers can cross-subsidise or bundle to win deals, undermining Cloudflare’s ability to sustain pricing without corresponding feature depth.
The core risk is cost overhang without corresponding revenue leverage. This could erode gross margin and reduce Cloudflare’s ability to reinvest.
E) Strategic coherence and bundle fragility
Cloudflare’s platform ambition, being the “Connectivity Cloud”, rests on a coherent vision: an integrated suite where every part amplifies the others. But expansion brings risk: is the bundle still additive, or simply broad?
Category creep: Cloudflare now spans security, compute, storage, observability, AI inference. The risk is that few of these domains are deep enough to dominate and together, they may confuse rather than compel.
Buyer misalignment: Storage, compute, and observability are typically bought by different teams on different timelines. A “one pane of glass” pitch may resonate with mid-market tech firms, but not with complex, siloed enterprises.
Dilution of focus: If the platform becomes sprawling, it may lose the polish and opinionation that made early products compelling. New users may see Cloudflare as a jack-of-all-trades - not a best-in-class anything.
Strategic coherence matters more than breadth. If the platform story breaks, Cloudflare loses the ability to pull expansion revenue across the suite and becomes vulnerable to modular challengers picking off high-margin verticals.
F) Execution complexity at scale
Cloudflare’s shipping cadence, infrastructure discipline, and cultural cohesion are among its greatest strengths. But scale introduces entropy. As the company grows in headcount, geography, and product scope, can it maintain operational velocity?
Coordination drag: More products mean more interdependencies. One misaligned launch (e.g. R2 limits, Workers billing) can stall multiple teams. The cost of cross-team orchestration rises nonlinearly.
Cultural dilution: The founder-led, engineering-heavy ethos that defines Cloudflare today may weaken as layers of management, compliance, and enterprise process accumulate. Speed decays. Boldness fades.
Talent and leadership depth: As the business shifts from product-led growth to strategic enterprise partnerships, Cloudflare will need different muscles including field sales, alliances, and customer success. Building those without losing its soul is a difficult feat.
If execution slips, the flywheel slows. Products stagnate. Innovation lags. And rivals with deeper vertical expertise or better customer support begin to outpace Cloudflare in enterprise settings.
Conclusion: A Platform of possibility, not certainty
Cloudflare stands at the convergence of multiple secular currents: cloud decentralisation, Zero Trust security, AI latency constraints, and a structural shift toward programmable infrastructure. It is not just selling services - it is trying to define the abstraction layer through which the modern internet is built, secured, and scaled. The ambition is enormous, the product velocity relentless, and the surface area of innovation (spanning performance, security, developer tooling, and compute) strategically expansive.
The size of the prize is large, with a TAM exceeding $100b and with real market momentum across multiple categories, and Cloudflare has the potential to become a default component in enterprise architectures. Its integrated platform approach, developer-first brand, and cloud-neutral stance create meaningful friction for rivals and allow for asymmetric leverage in cross-sell motions. The virtuous loop, where product usage fuels deeper integration (which in turn reinforces lock-in) could plausibly drive durable expansion.
Yet the path from potential to inevitability is steep.
Cloudflare's valuation embeds high expectations, requiring sustained high 20s revenue growth. If Cloudflare executes, compounding wallet share, embedding Workers as a credible compute layer, and building true Zero Trust depth, it could structurally reshape the cloud stack and justify its premium. But it must thread several needles to get there.
In sum: the opportunity is large, the moats are real, but the outcomes remain non-linear. Cloudflare is no longer just a CDN. It is a bet on convergence of security, performance, and compute at the edge, and a test of whether infrastructure platforms can earn not just usage, but trust.
The market will reward execution. But it will not forgive its absence.
Subscribe for thoughtful, in-depth analysis of the world’s most impactful companies—delivered directly to your inbox.
If you enjoyed this piece, a like is always appreciated!
Sources
Disclaimer
This article is provided for information purposes only. This article has been prepared based upon information, including market prices, data and other information, from sources believed to be reliable, but the authors do not warrant its completeness or accuracy. Any opinions and estimates constitute our judgment as of the date of this material and are subject to change without notice. Past performance is not indicative of future results. This article is not intended as an offer or solicitation for the purchase or sale of any financial instrument. The authors do not provide individually tailored investment advice. Any opinions and recommendations herein do not take into account individual circumstances, objectives, or needs and are not intended as recommendations of particular securities, financial instruments or strategies. You must make your own independent decisions regarding any securities, financial instruments or strategies mentioned or related to the information herein.