Zscaler: Zero Trust, or Zero Differentiation?
A deep dive into Zscaler’s evolution, $277b market opportunity, and the competitive threats challenging its role as the control point in Zero Trust security.
Zscaler’s founding bet — that legacy VPN- and firewall-centric architectures would fail in a cloud-first world — has been vindicated, and its Zero Trust Exchange now brokers traffic for thousands of enterprises and tens of millions of users across a global footprint.
But the next decade will be harder.
Zscaler sits at the fault line between two market forces: platforms collapsing networking and security into bundled cloud stacks, and best-of-breed specialists carving out depth in high-value niches.
Microsoft can bundle “good enough” SSE into E5, Cloudflare can extend its global edge network into full Zero Trust, and cloud-security pure-plays like Wiz, Illumio and Armis can out-innovate in narrow domains.
The investor questions are twofold: can a neutral security control point defend pricing power and relevance as platform integration accelerates, and can Zscaler expand product depth fast enough to remain the system-of-record for secure access, rather than a pass-through policy layer? We aim to answer these questions over a 2-part series.
Part 1 examines Zscaler’s founding insight, the structural drivers shaping demand, and today’s competitive map. Part 2 tests the durability of its economics under Hamilton Helmer’s “7 Powers” lens and assesses valuation and risk-reward under multiple competitive and macro scenarios.
At Pumice Capital, we publish free, in-depth fundamental research on high-quality companies built to compound over decades. Our focus is a concentrated portfolio of resilient, growth-driven businesses with a 10+ year horizon — backed by deep, differentiated analysis rarely found in mainstream coverage.
Recent reports: Cloudflare (NET) | Confluent (CFLT) | Snowflake (SNOW)
If you want early access to our latest research on the companies shaping the future, you can subscribe for free today.
1 – Why Zscaler exists
“Our mission is to empower organizations to realize the full potential of the cloud and mobility by securely connecting users to applications from any device, anywhere”
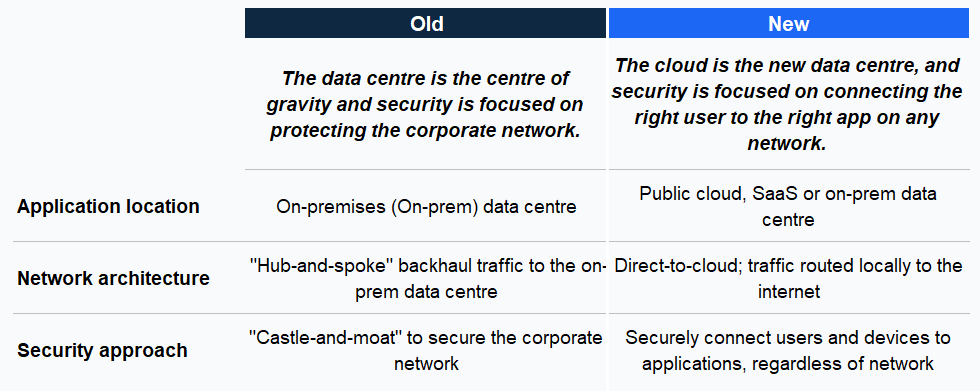
When Jay Chaudhry founded Zscaler in 2007, he was convinced “the castle-and-moat model of corporate security was crumbling.” SaaS, mobile devices, and direct-to-internet workflows were rendering hub-and-spoke networks “slow, costly, and fundamentally unsafe once the perimeter was breached.” His aim was to move security “out of the box in the data centre and into a utility for the internet age” — a multi-tenant, globally distributed service that could connect any user to any app, from any device, anywhere.
Even the name reflected the ambition: a portmanteau of “Zenith of Scalability,” signalling a vision of internet-wide security unconstrained by hardware limits or geography.
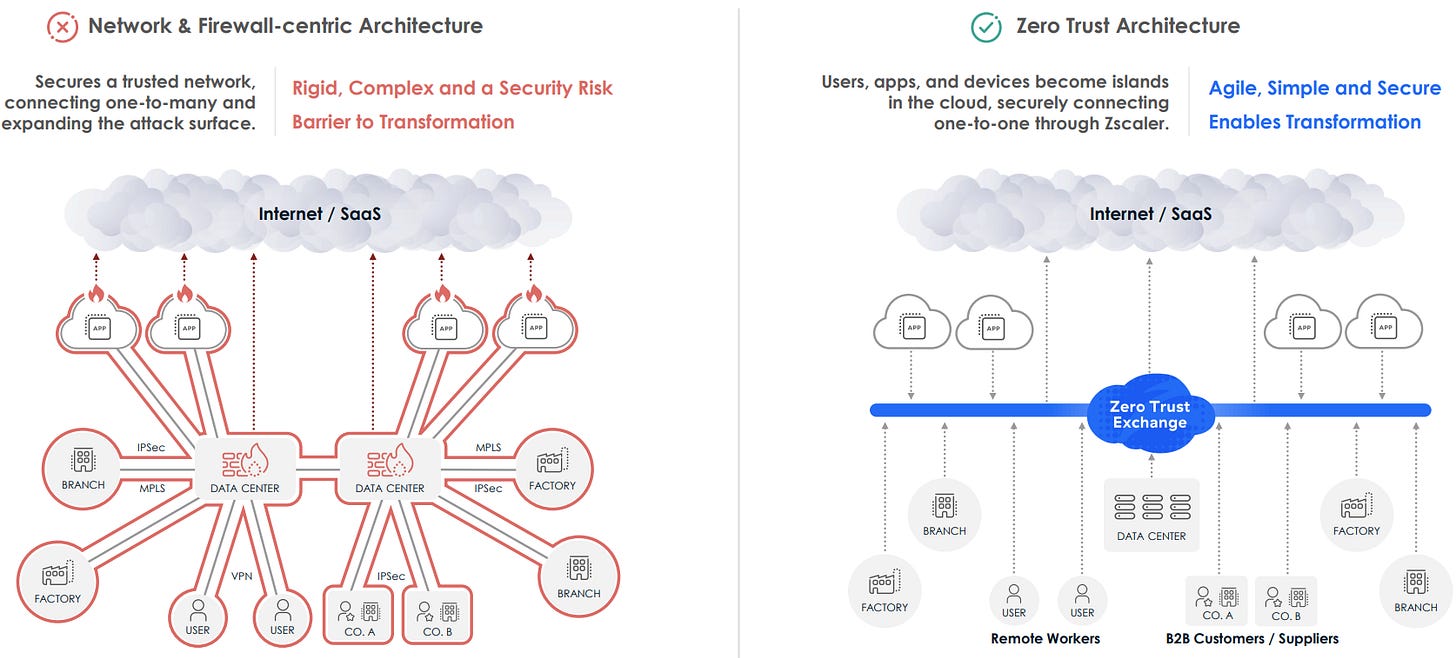
Instead of placing users on a network they could roam freely inside, his Zero Trust model would authenticate every session, connect it only to the specific app or service required, and inspect all traffic inline at cloud scale. In Chaudhry’s view, that was the only way enterprises could fully embrace the agility and reach of the cloud without importing the risks of the old perimeter.
The below chart highlights the differences in old vs. new security approaches:
Legacy vs. modern security approaches
Early product development
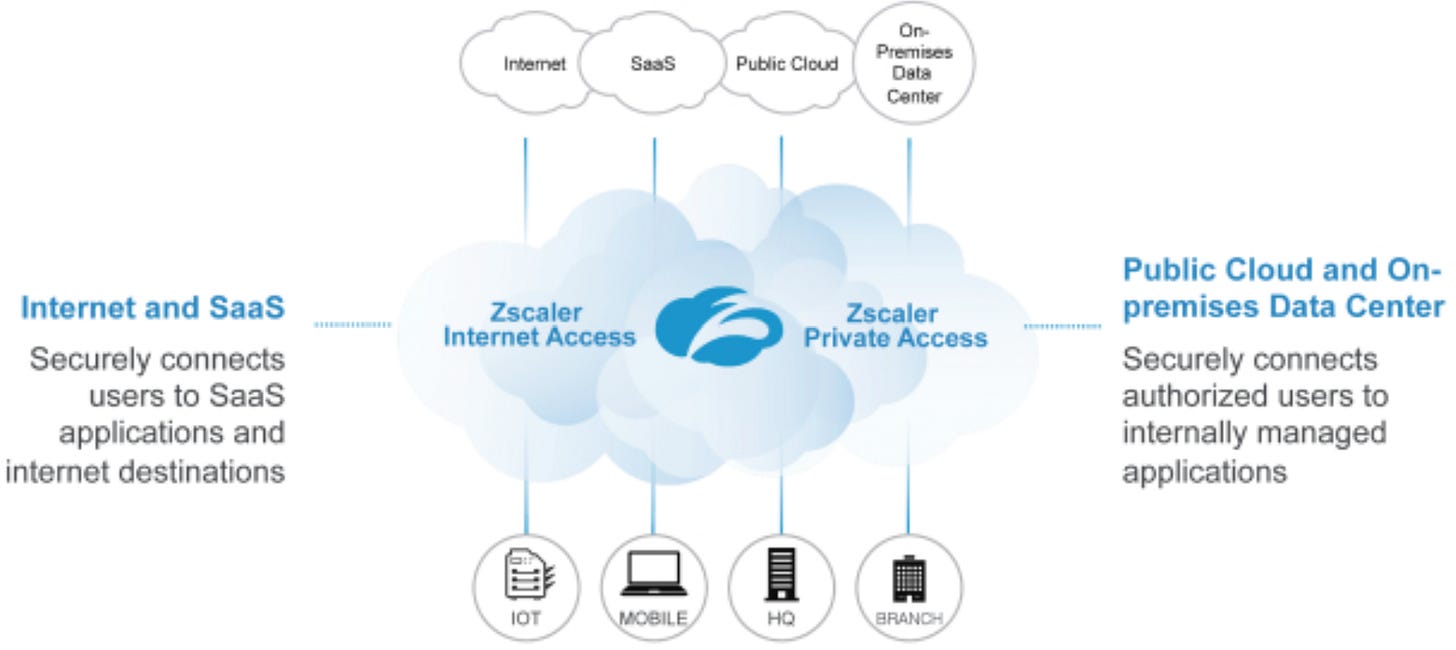
Zscaler Internet Access (ZIA): Solving real pain points in the early 2010s
Zscaler’s first commercial proof point was Zscaler Internet Access (ZIA), launched in the early 2010s to secure outbound internet traffic in the cloud. Chaudhry recalls, “Selling security without appliances was a radical idea — we had to show CIOs it could work better than the hardware they trusted.”
ZIA explained: ZIA is like a cloud-based security checkpoint for internet traffic. It applies your company’s security policies and scans for threats before anything reaches your device — no matter where you're working. This removes the need to route traffic through a central data centre, which boosts performance, simplifies IT management, and scales easily as your team grows.
From a competitive standpoint, ZIA's early traction served as proof that cloud-native performance and scalability could win against entrenched appliance incumbents. This was critical in convincing risk-averse enterprises to move core security functions off-premises.
As SaaS adoption surged in the mid-2010s, appliance-based tools became increasingly slow, complex, and costly. Although large enterprises required time and education to shift, ZIA’s benefits (faster performance, reduced IT overhead, and easier scalability) ultimately drove widespread adoption.
Enter ZPA (2015–2017): Extending cloud-native access to internal apps
With that initial foothold, Zscaler extended the Exchange into private application access with Zscaler Private Access (ZPA) between 2015 and 2017. Chaudhry argued, “Why put a user on the entire network when they only need one app?”. ZPA replaced VPNs with identity-based, app-specific connections, sharply reducing lateral-movement risk and containing breaches before they spread.
ZPA explained: Instead of placing users on the corporate network (where they could potentially access other systems), ZPA creates identity-verified, direct connections to specific applications. This approach significantly reduces lateral movement risk, which is the ability of attackers to move across systems within a network after gaining initial access. By eliminating broad network access, ZPA helped to contain threats and limit potential damage from compromised users.
Strategically, ZPA expanded Zscaler’s addressable market beyond internet-bound traffic, deepened integration into customer environments, and reduced reliance on a single revenue stream. While early deployments required tuning, customer feedback highlighted strong visibility and segmentation benefits, and independent studies later reported measurable ROI and breach-rate reductions (Forrester reported a 289% average ROI and a 55% drop in breaches among ZPA users in 2024.).
Pandemic acceleration and expanding use cases
The shift to remote work in 2020 exposed the latency and reliability limits of corporate VPN infrastructures. For enterprises already using ZIA, adding ZPA provided a direct path to extend secure internal application access without the performance penalties of backhaul. Chaudhry noted, “In weeks, customers went from ‘we’ll pilot ZPA’ to ‘we need it for the whole workforce by Monday’.”
This urgency accelerated multi-product adoption within the installed base and broadened ZPA’s role beyond employee access. Enterprises increasingly used it to connect contractors, partners, and third-party developers to specific applications without exposing the wider network, reinforcing Zscaler’s positioning as a universal access broker rather than a remote-work point solution.
Zscaler ZIA and ZPA
Platform expansion and IPO
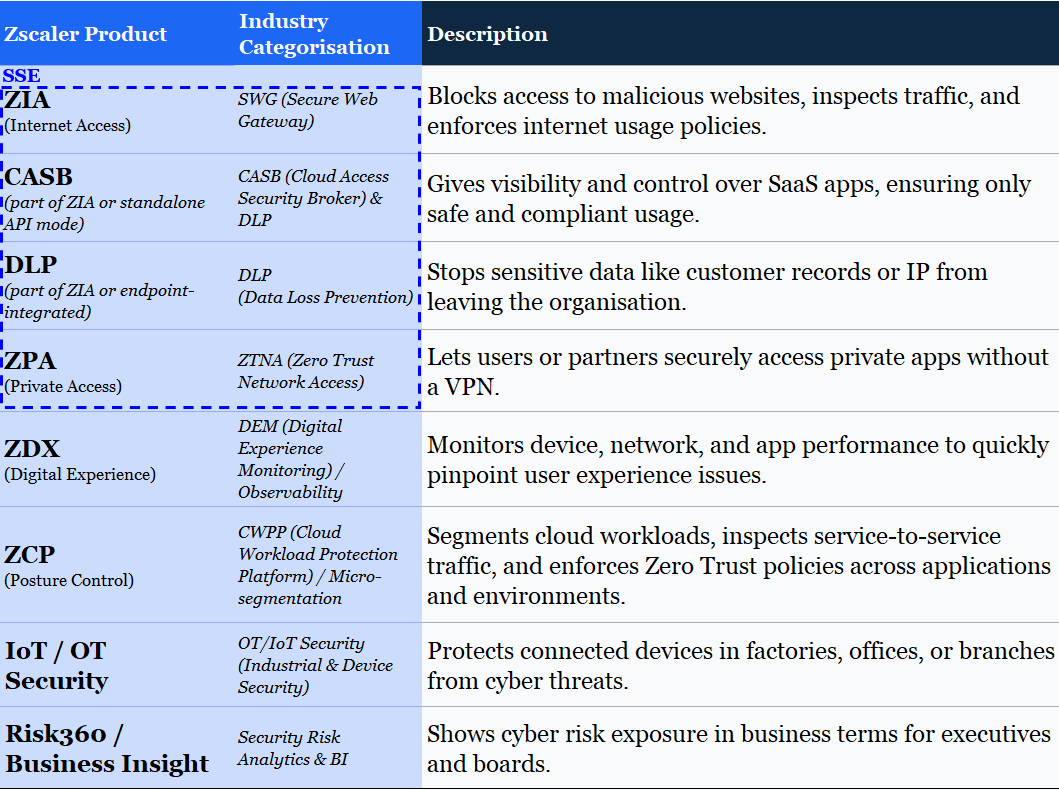
With ZIA and ZPA established, Zscaler broadened the Zero Trust Exchange into adjacent security and networking functions to increase share of wallet and embed more deeply into customer environments. Major additions include:
Workload Communications (Zscaler Cloud Protection – ZCP, 2020): Segments and secures east–west traffic between cloud workloads, reducing the attack surface inside public cloud environments. Strengthens Zscaler’s relevance to DevOps and cloud security teams.
Digital Experience Monitoring (Zscaler Digital Experience – ZDX, 2020): Provides end-to-end visibility into user experience and application performance, enabling IT teams to troubleshoot without on-premises appliances. Improves retention by integrating performance management with security.
B2B and OT/IoT extensions (IoT/OT Security, 2021–2022): Applies Zero Trust principles to partner access, industrial control systems, and IoT devices, addressing security gaps in manufacturing, energy, and critical infrastructure sectors. Expands TAM beyond the traditional corporate workforce.
Security posture management and risk analytics (Risk360 and Zscaler Business Insights – BI, 2023): Combines cloud security posture management (from acquisitions) with analytics on policy gaps, risk scoring, and compliance tracking. Adds preventative and governance layers on top of inline enforcement, supporting executive and board-level reporting.
Security workflow automation (ShiftRight acquisition, 2021): Integrates incident response, policy updates, and remediation into customer workflows, improving operational efficiency for SOC teams and driving platform stickiness.
These expansions positioned Zscaler to address a larger share of the Secure Service Edge (SSE) and Zero Trust markets, while creating more entry points for cross-sell within existing accounts. However, they also broadened the competitive set to include multi-product platforms like Microsoft, Palo Alto Networks, and Cloudflare, requiring continued investment to match their breadth and integration.
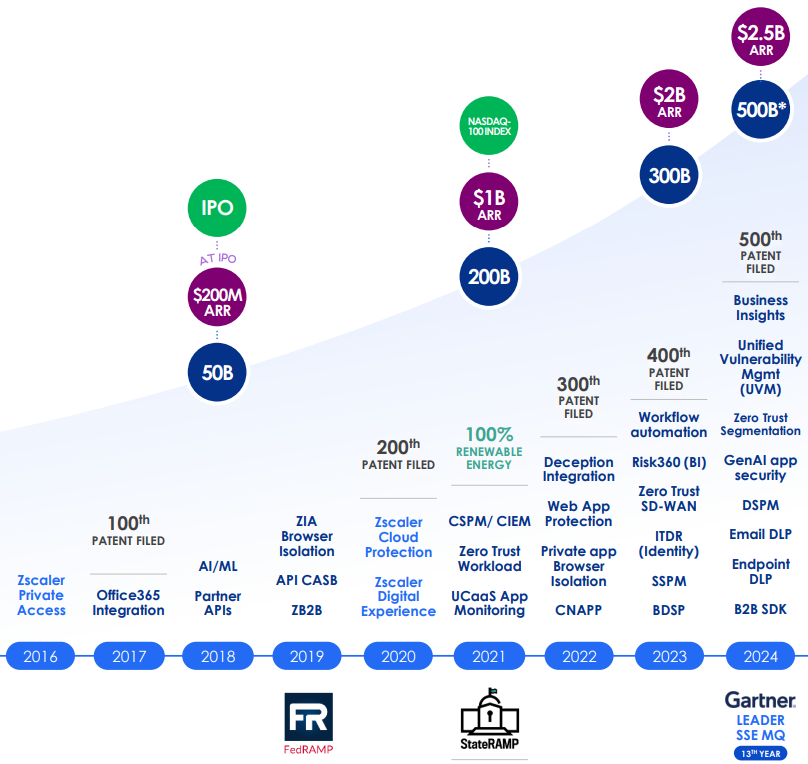
In March 2018, Zscaler completed its IPO, raising $192m at a c.$3.6bn valuation. The listing increased market visibility, provided capital for R&D and acquisitions, and enhanced credibility in pursuing large enterprise and government contracts. Since then, ARR has grown at a c.52% CAGR (2018-2024), with multi-product adoption steadily increasing as the platform strategy has matured.
Zscaler product development: 2016 to 2024
In Q1 FY25, Zscaler’s Zero Trust Exchange processed more than 500 billion daily transactions for approximately 8,600 customers and over 47 million users worldwide. Each transaction represents a real-time security or access decision — from inspecting web traffic and brokering application sessions, to scanning content for data loss prevention or enforcing microsegmentation across internal workloads.
This section has traced the evolution of Zscaler’s product suite — from ZIA and ZPA through to newer offerings like ZDX, IoT/OT Security, Risk360, and ZCP — and how these expansions have positioned the company across a broader swathe of the Secure Service Edge and Zero Trust markets. The next section looks forward, assessing how these capabilities are expected to develop and the structural trends likely to underpin growth over the next five to ten years.
Zscaler product recap
2 – Market growth drivers
Historical growth context
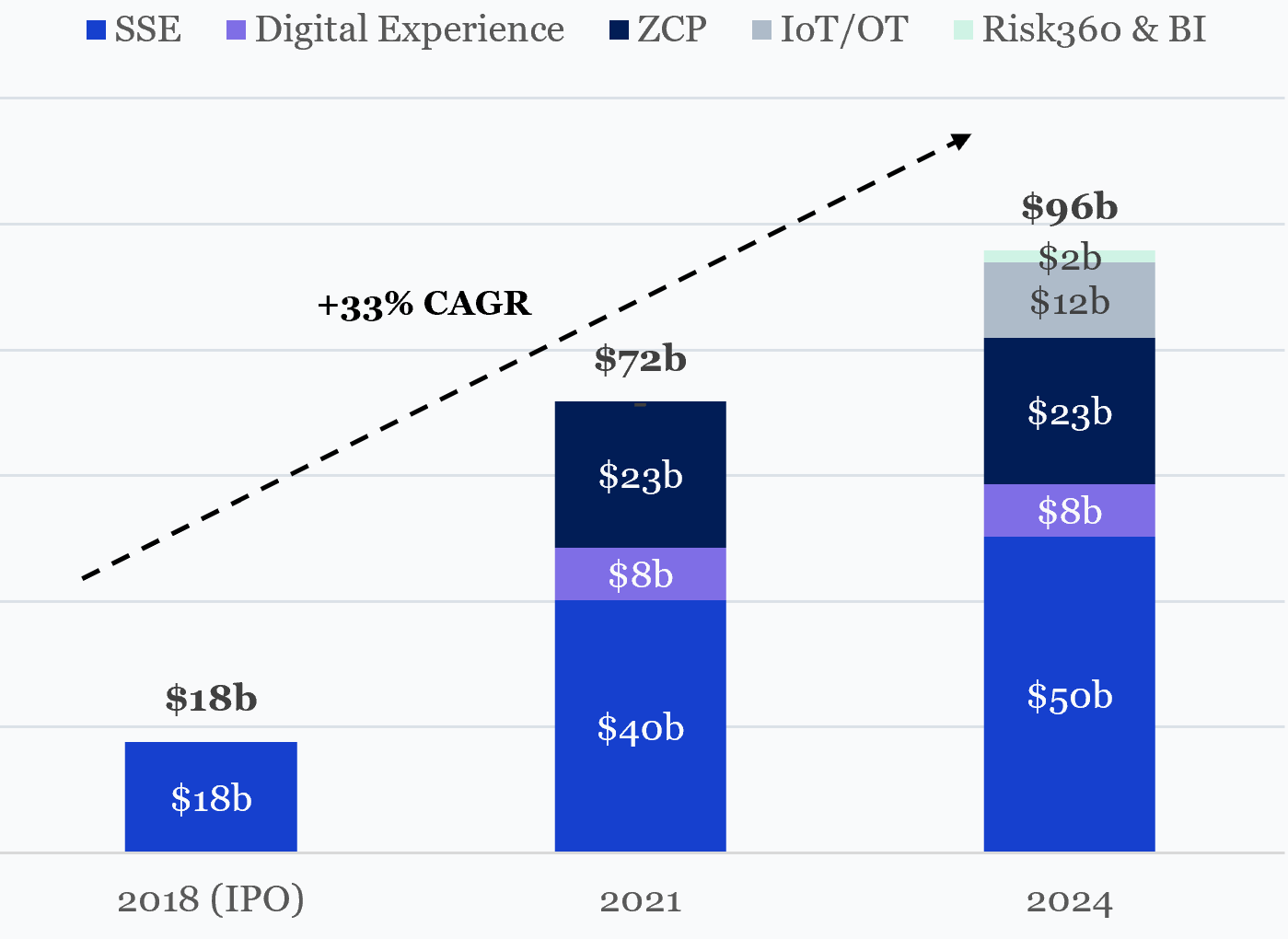
Since its IPO in 2018, Zscaler’s serviceable addressable market (SAM) has expanded from $17.7bn (IDC’s assessment of what customers spend on like-for-like products) to $96bn in FY24. This growth reflects both the modernisation of legacy security budgets and the creation of entirely new, cloud-native security categories rooted in Zero Trust.
Zscaler’s Serviceable Addressable Market: 2018 to 2024
A) Legacy modernisation (c.35% / c.$27b of SAM growth)
With more than 50% of enterprise workloads now hosted in Microsoft 365, Salesforce, AWS, and Azure, routing traffic through centralised firewalls has become impractical.
Impact: Budgets tied to SWG and VPN appliances (Blue Coat, Cisco ASA) migrated to cloud-delivered SSE platforms (ZIA and ZPA).
B) Incumbent displacement (c.20% / c.$16b of SAM growth)
Hybrid work and growing SaaS adoption have made IT environments more complex and fragmented. As trust shifted to users and devices, many legacy CASB appliances became obsolete.
Impact: Zscaler consolidated spend from standalone CASB/DLP (Skyhigh, Symantec) and firewall-based egress filtering (Palo Alto, Fortinet) by embedding these functions within its SSE platform.
C) Cloud-native category expansion (c.45% / c.$35b of SAM growth)
Decentralised IT and hybrid work created security gaps that legacy tools couldn’t address.
Impact: New needs like securing internal workload traffic, monitoring user experience, protecting IoT/OT environments, and applying AI to risk policy, drove demand for cloud-native solutions. Zscaler extended beyond ZIA/ZPA into these areas, unlocking growth in markets that barely existed in 2018.
Growth outlook
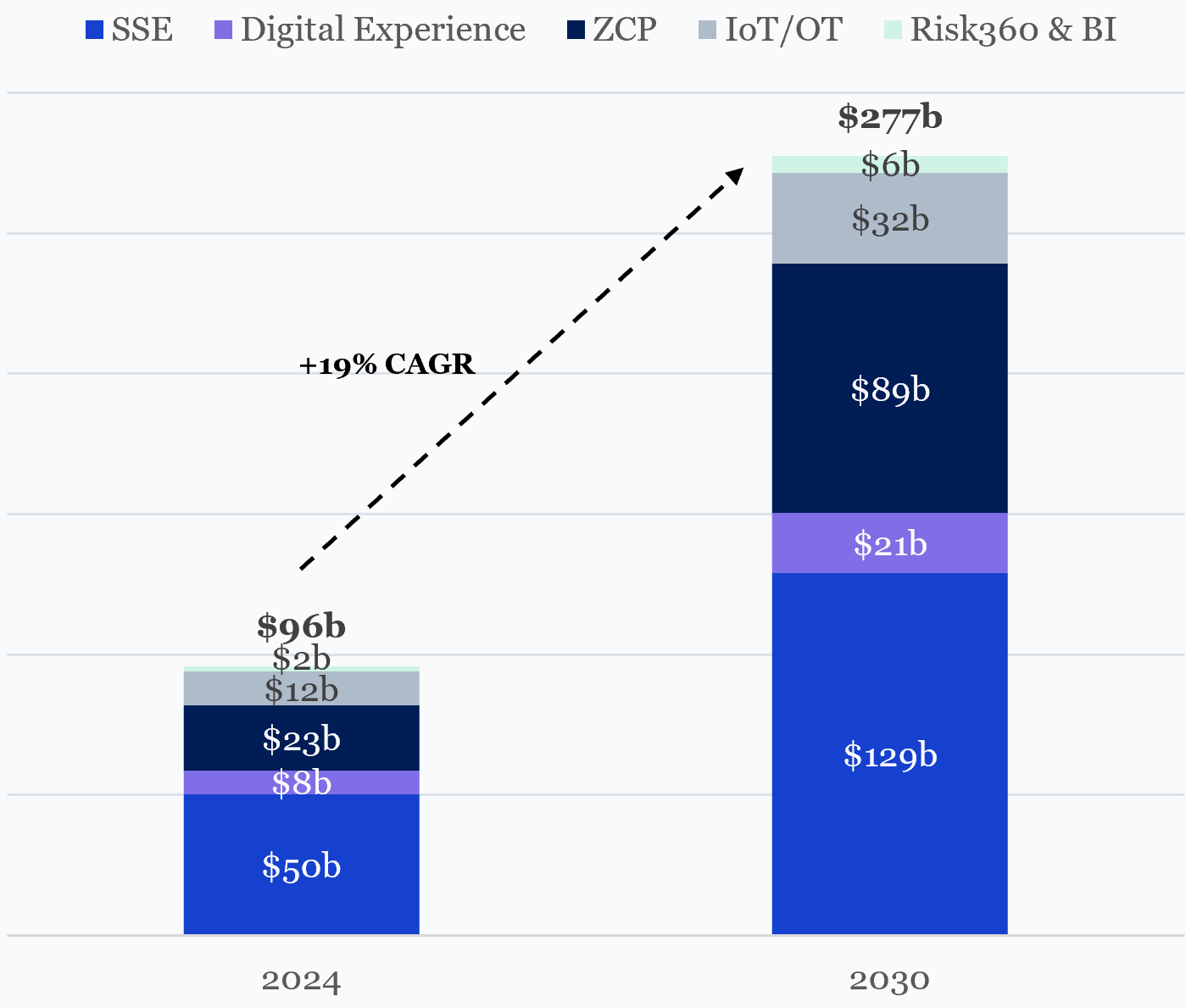
Industry growth is forecast to continue at 19% annually, increasing the company’s SAM to $277b by 2030, underpinned by a continuation and evolution of the trends already at play today, namely:
The transition of all workflows to the cloud
Rising compliance and regulatory scrutiny
The rise of ‘work anywhere’ on ‘any device’
A proliferation in bad actors trying to take advantage of the rapidly evolving technological landscape
Zscaler’s Serviceable Addressable Market: 2024 to 2030
A) SSE: Ongoing cloud proliferation (c.43% / c.$80b of SAM growth)
SSE remains Zscaler’s largest and most important opportunity, accounting for roughly half of its total addressable market. Gartner’s SSE Market Forecast 2024 projects a 16–18% CAGR through 2030, underpinned by:
Long-tail modernisation: Many large enterprises continue to decommission legacy appliances. For example, in 2024 BP retired over 60% of its firewall stack after migrating to Microsoft 365 and AWS, deploying ZIA and ZPA to c.80,000 employees and reducing VPN-related incidents by 70%.
Rising compliance complexity: With over 50 countries enforcing data localisation, demand for sovereign cloud solutions is surging. Zscaler’s global cloud and in-line architecture (embedding security directly into the data path) enable real-time inspection, lower latency, and seamless compliance, unlike bolt-on or gateway-based approaches used by competitors.
B) Digital Experience Market: Structural movement to hybrid work (c.7% / c.$13b of SAM growth)
ZDX strengthens Zscaler’s platform differentiation by embedding real-time user experience insights alongside core SSE and workload protection - providing a natural upsell path and improving operational outcomes for IT teams. Mordor Intelligence forecasts the Digital Experience Monitoring (DEM) market to grow at a c.17% CAGR through 2030, driven by:
Infrastructure fragmentation: Despite widespread SaaS adoption, most enterprises still operate across hybrid environments (mixing on-prem, cloud, and third-party services). This fragmentation makes it difficult to diagnose performance and connectivity issues across networks.
Hybrid work persistence: Post-pandemic, hybrid work is the norm. As users operate outside managed networks, IT teams need tools to pinpoint device, app, or network issues without relying on legacy, on-prem monitoring systems.
Tool consolidation: Enterprises are moving away from using separate point tools like ThousandEyes, Nexthink, or Riverbed for network and device monitoring. Instead, they’re adopting integrated platforms that combine these capabilities—simplifying operations and cutting costs
C) Workload Security: Increasing “east-west” traffic (c.36% / c.$65b of SAM growth)
Zscaler entered the workload security market in 2020, and it now represents its largest growth opportunity outside SSE. Gartner projects >25% CAGR through 2030 for Zero Trust workload security, driven by:
Modern app architectures: As companies move from single, monolithic apps to smaller, distributed services, internal traffic between systems is expected to make up 70–80% of enterprise network flows. This increases the risk of threats spreading inside the network, and traditional security tools often can’t see or control this traffic—leaving blind spots.
Microsegmentation: Key to limiting breach impact by isolating workloads. As internal environments grow more dynamic and distributed, segmentation becomes critical to enforcing Zero Trust and securing cloud-native workloads beyond the reach of traditional firewalls.
Regulatory scrutiny: Sectors like finance and healthcare now face stricter rules around breach containment, segmentation, and auditability. This drives demand for security architectures that can enforce policy and provide clear visibility across environments.
D) IoT/OT security: bridging IT and industrial domains (c.11% / c.$20b of SAM growth)
Although more nascent, OT security is rapidly emerging as a strategic priority, particularly in critical infrastructure. IDC projects a c.18% CAGR through 2030. Zscaler is well positioned to capitalise via:
Rising investment in critical sectors: Industries like energy, manufacturing, and transportation face increasing attacks on operational systems, prompting greater security spending to protect uptime, safety, and supply chains.
Shift toward unified IT–OT security: Enterprises are moving away from siloed industrial tools in favour of cloud-native platforms that can enforce consistent Zero Trust policies across both corporate and operational networks.
Regulatory pressure: Standards like NIS2 in Europe and sector-specific mandates in the US require better segmentation, monitoring, and incident response in OT environments.
E) Risk360/ BI SAM: AI-powered threats and AI-augmented security (c.2% / c.$4b of SAM growth)
Though Risk360/BI remains Zscaler’s smallest SAM, it is strategically significant as enterprises face a sharp rise in AI-driven threats - up fivefold since 2021. Gartner forecasts ~20% CAGR through 2030, driven by:
AI-powered detection and telemetry: As threats become more sophisticated and evasive, enterprises are adopting AI to detect behavioural anomalies and assess risk in real-time - an area where Zscaler’s telemetry scale (500B+ daily events) provides a clear advantage.
Automated threat correlation: Reducing mean-time-to-detect (MTTD) requires correlating signals across users, apps, and workloads. Zscaler’s unified architecture enables this cross-surface visibility and response automation.
Embedded risk analytics in policy enforcement: Zscaler’s integration of AI into ZIA/ZPA enables dynamic access decisions based on real-time risk posture - deepening its value proposition as not just a secure access layer, but a smart, adaptive one.
These market drivers underpin Zscaler’s continued growth trajectory, albeit in a landscape marked by intensifying competitive pressures, especially from hyperscalers and security incumbents aggressively pivoting towards SSE offerings. The next section examines how robustly Zscaler’s competitive positioning can withstand these emerging challenges.
3 - Competitive landscape
Zscaler’s competitive set spans four distinct groups, each defined by its primary market identity and go-to-market positioning. Zscaler tends to win where its cloud-native, unified SSE architecture and track record of large-scale enterprise deployments translate into measurable operational and security gains.
Full-stack SSE competitors – Compete on perceived simplicity and existing relationships, often leveraging networking refresh cycles.
Product specialists – Win with deep, best-of-breed capabilities in discrete niches.
Platform-embedded security – Offer “good enough” tools deeply integrated into broader productivity, identity, or cloud ecosystems.
Mid-market price attackers – Target cost-sensitive buyers with lighter-weight, lower-priced SSE solutions.
To sustain leadership, Zscaler must:
Deepen SD-WAN integration and routing parity while positioning Zero Trust SD-WAN as a step-change architecture.
Match or exceed best-in-class depth in high-growth adjacencies (e.g., CSPM, microsegmentation).
Defend against hyperscaler bundling by demonstrating operational superiority, especially in multi-cloud and regulated sectors.
A) Full-stack SSE competitors (highest substitution risk)
Broad SSE/SASE platforms with strong brands, distribution, and R&D capacity capable of displacing Zscaler as the default enterprise security layer. Many are expanding into adjacencies like cloud workload security and digital experience monitoring.
Examples: Palo Alto Networks, Cisco, Fortinet, Netskope.
Go-to-market: Converged security plus SD-WAN, often tied to networking refresh cycles, supported by aggressive discounting. Note: SASE = SSE + SD-WAN under one operating model.
Threat scope:
SSE: Direct substitution risk for ZIA/ZPA. Cloud-native peers (e.g., Netskope) are competitive in greenfield deployments, while PANW/Fortinet/Cisco hold an advantage in hybrid environments aligned to networking refresh cycles.
Adjacencies: PANW’s Prisma Cloud overlaps with ZCP; Cisco’s ThousandEyes competes with ZDX; all are adding IoT/OT modules.
Where Zscaler wins:
Cloud-native, multi-tenant architecture with global PoP performance.
Identity-driven, cross-platform policy model.
WAN-agnostic integration, including Zero Trust SD-WAN.
Where Zscaler loses:
Perceived appliance simplicity and one-vendor appeal for network plus security.
Entrenched networking procurement relationships.
CASB depth in certain verticals (Netskope).
Latency-sensitive SD-WAN perceptions in hardware-led deployments.
Investor view: This is the most strategically important battleground. Defending SSE leadership here is critical to sustaining attach momentum in adjacencies and maintaining pricing discipline.
B) Product specialists (partial wallet share risk)
Focused players with best-in-class depth in specific security or monitoring functions.
Examples: Wiz, Illumio, Armis, Dynatrace, New Relic, Catchpoint
Go-to-market: Domain-specific expertise delivered via specialist tooling.
Threat scope:
ZCP: Wiz leads in developer-first CSPM/CNAPP; Illumio dominates microsegmentation.
IoT/OT: Armis provides broader unmanaged device visibility and OT protocol coverage.
ZDX: DEM vendors (Catchpoint, Dynatrace, New Relic) offer deeper app-level instrumentation.
Where Zscaler wins:
Single-source procurement trends: Gartner projects >60% of new SSE deployments will be sourced from single-vendor stacks by 2027, up from <20% in 2023.
Ability to add capabilities without requiring separate systems or management layers.
Unified policy and analytics across users, workloads, and devices.
Where Zscaler loses:
Specialist feature depth, especially in developer-first security and OT protocol coverage.
Faster adoption cycles in niche markets not tied to SSE procurement.
Investor view: Low substitution risk for core SSE, but meaningful TAM erosion if attach rates in adjacencies stall. Risk increases in a slower SSE growth environment.
C) Platform-embedded security (pricing and bundling risk)
Security integrated into broader productivity, cloud, or edge platforms, often bundled at low or zero incremental cost.
Examples: Cloudflare, Microsoft, Google.
Go-to-market: SSE-adjacent security embedded into broader ecosystems.
Threat scope:
SSE: Microsoft offers ZTNA, SWG, CASB in E5; Google embeds security into GCP; Cloudflare delivers ZTNA/SWG via its edge network.
Adjacencies: Microsoft Defender for Cloud overlaps ZCP; Cloudflare’s network observability touches ZDX-adjacent areas.
Where Zscaler wins:
Multi-cloud neutrality with consistent enforcement across environments.
Independence from productivity/cloud provider roadmaps.
Security-first architecture and SLA-backed performance.
Where Zscaler loses:
Perceived sufficiency of bundled “good enough” tools.
Deep native integration with each vendor’s broader stack.
Investor view: Pricing pressure and slowed expansion velocity are the primary risks, particularly in Microsoft/Google standardised environments. Cloudflare’s edge-centric execution adds an architectural challenge over the medium term.
D) Mid-market price attackers (cost-driven risk)
Lower-priced SSE offerings targeting mid-sized enterprises and budget-conscious buyers.
Examples: iboss, Skyhigh Security
Go-to-market: Streamlined SSE at materially lower ASPs, with limited adjacency scope.
Threat scope:
Compete mainly in SWG/ZTNA at lower cost; minimal enterprise penetration.
Where Zscaler wins:
Superior efficacy, scalability, and enterprise-grade SLAs.
Where Zscaler loses:
Lowest-price wins in cost-first buying cycles.
Investor view: Limited impact on enterprise growth but caps penetration in lower-margin market tiers.
From Origins to Inflection Point
Zscaler’s trajectory to date reflects a rare combination of timing, architectural vision, and execution discipline. The shift away from perimeter-based models has created a structural tailwind for cloud-native security platforms, and Zscaler’s position as a neutral, globally distributed control point has so far allowed it to capture disproportionate share. Its expansion from ZIA into ZPA, workload protection, and digital experience monitoring shows a clear intent to deepen its role across security workflows, increasing both switching costs and share of wallet.
Yet the competitive terrain is tightening. Hyperscalers are embedding security into bundled offerings at negligible marginal cost, while Cloudflare and other edge-first challengers are converging on similar Zero Trust architectures. Specialist vendors continue to innovate rapidly in targeted niches, offering depth that can lure high-value workloads away from broad platforms.
The core investor questions therefore remain unresolved: can Zscaler defend pricing power and strategic relevance as integration accelerates, and can it grow product depth fast enough to remain the enterprise system-of-record for secure access rather than a commoditised policy layer?
These are the questions Part 2 will address — first by stress-testing Zscaler’s competitive position and economic resilience through the lens of Hamilton Helmer’s “7 Powers,” and then by examining the valuation, scenario outcomes, and risk-reward profile implied by today’s market price.
Sources
Agence nationale de la sécurité des systèmes d'information (ANSSI) (2024) – SecNumCloud Compliance Requirements.
Center for Strategic and International Studies (CSIS) (2024) – Global Data Sovereignty and Localisation Laws Tracker
CSIS (2024) – Global Data Sovereignty Tracker
European Union Agency for Cybersecurity (ENISA) (2024) – NIS2 Directive Implementation Timeline
Gartner (2024) – Cloud Shift: The Future of Enterprise Workloads. Gartner Research
Gartner (2024) – AI in Security Forecast: Augmented Cyber Operations by 2030
Gartner (2024) – Cloud Compliance Forecast
Gartner (2024) – Microsegmentation and East-West Workload Security Forecast 2024–2030
Gartner (2024) – SSE Market Forecast
Gallup (2024) – State of the Workplace 2024: Hybrid and Remote Work Trends
Gartner (2024) – Zero Trust Networking and Workload Security Forecast
IBM Security (2024) – Cost of a Data Breach Report: OT and Industrial Cybersecurity Trends
IDC (2024) – Industrial Cybersecurity and OT Threat Landscape Report
Microsoft (2024) – Digital Defense Report 2024: AI-driven Threat Landscape
Ministry of Electronics and Information Technology (MeitY), India (2024) – Digital Personal Data Protection Act (DPDP) Guidelines
Mordor Intelligence (2024) – Digital Experience Monitoring Market Report
Office of Management and Budget (OMB) (2022) – M-22-09: Federal Zero Trust Strategy
SANS Institute (2024) – ICS/OT Cybersecurity Survey
Disclaimer
This article is provided for information purposes only. This article has been prepared based upon information, including market prices, data and other information, from sources believed to be reliable, but the authors do not warrant its completeness or accuracy. Any opinions and estimates constitute our judgment as of the date of this material and are subject to change without notice. Past performance is not indicative of future results. This article is not intended as an offer or solicitation for the purchase or sale of any financial instrument. The authors do not provide individually tailored investment advice. Any opinions and recommendations herein do not take into account individual circumstances, objectives, or needs and are not intended as recommendations of particular securities, financial instruments or strategies. You must make your own independent decisions regarding any securities, financial instruments or strategies mentioned or related to the information herein.